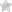Dear Readers,
In this article,we will see brief introdution on CloudTrail and view and download event from the last 90 days in the event history.

What is CloudTrail?
AWS CloudTrail is a service that enables governance, compliance, operational auditing, and risk auditing of your AWS account.
With CloudTrail, you can log, continuously monitor, and retain account activity related to actions across your AWS infrastructure.
CloudTrail provides event history of your AWS account activity, including actions taken through the AWS Management Console, AWS SDKs, command line tools, and other AWS services.
Event history simplifies security analysis, resource change tracking, and troubleshooting.
How CloudTrail Works
CloudTrail is enabled on your AWS account when you create it. When activity occurs in your AWS account, that activity is recorded in a CloudTrail event. You can easily view events in the CloudTrail console by going to Event history.
Event history allows you to view, search, and download the past 90 days of activity in your AWS account.
You can create two types of trails for an AWS account
A trail that applies to all regions
When you create a trail that applies to all regions, CloudTrail records events in each region and delivers the CloudTrail event log files to an S3 bucket that you specify.
A trail that applies to one region
When you create a trail that applies to one region, CloudTrail records the events in that region only. It then delivers the CloudTrail event log files to an Amazon S3 bucket that you specify
Benefits
Simplified compliance
With AWS CloudTrail, simplify your compliance audits by automatically recording and storing event logs for actions made within your AWS account. Integration with Amazon CloudWatch Logs provides a convenient way to search through log data, identify out-of-compliance events, accelerate incident investigations, and expedite responses to auditor requests.
Visibility into user and resource activity
AWS CloudTrail increases visibility into your user and resource activity by recording AWS Management Console actions and API calls. You can identify which users and accounts called AWS, the source IP address from which the calls were made, and when the calls occurred.
Security analysis and troubleshooting
With AWS CloudTrail, you can discover and troubleshoot security and operational issues by capturing a comprehensive history of changes that occurred in your AWS account within a specified period of time.
Security automation
AWS CloudTrail allows you track and automatically respond to account activity threatening the security of your AWS resources. With Amazon CloudWatch Events integration, you can define workflows that execute when events that can result in security vulnerabilities are detected. For example, you can create a workflow to add a specific policy to an Amazon S3 bucket when CloudTrail logs an API call that makes that bucket public.
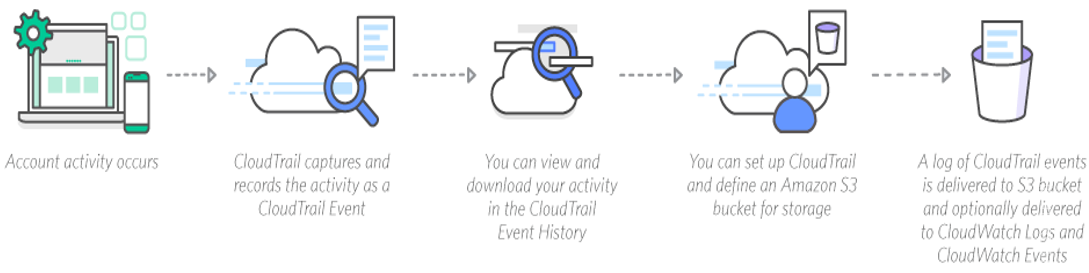
CloudTrail Supported Regions
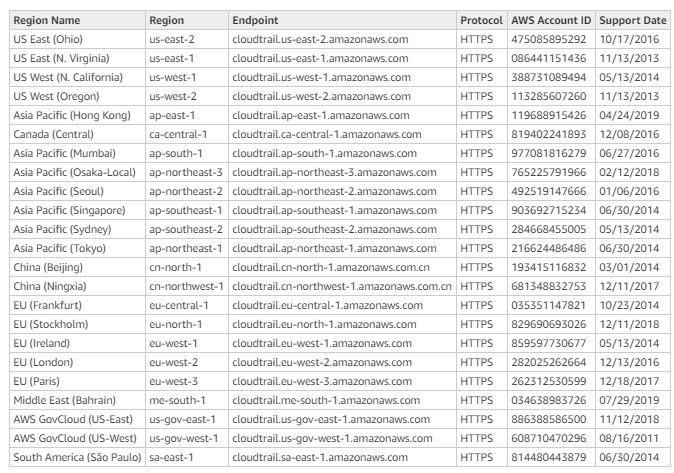
Limits in Amazon CloudTrail
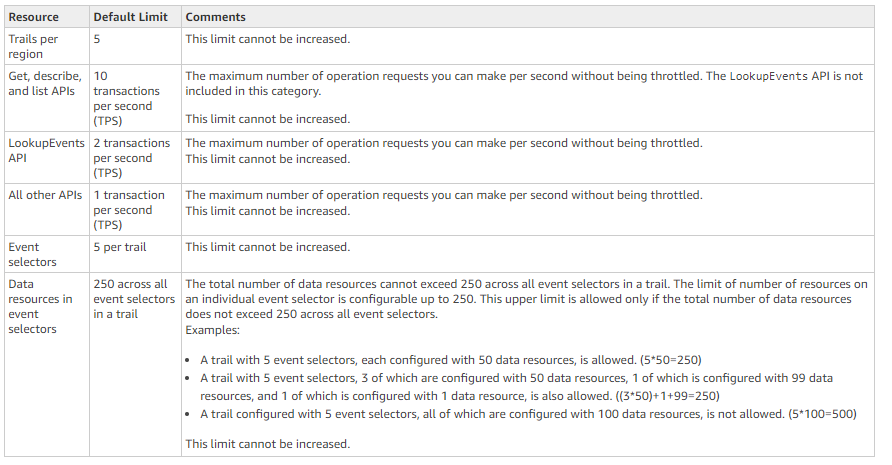
Using CloudTrail and Lambda together
CloudTrail generates a log entry for every API call made on your account. CloudTrail aggregates the log entries in JSON text files, zips the files, and copies them to the Amazon S3 bucket configured to receive CloudTrail log files.
The log parsing logic is deployed as a Lambda function. The Lambda function is triggered when CloudTrail copies a new file to your S3 bucket.
The Lambda function uses a configuration file that contains a list of specific API keywords that, when detected, will trigger a notification. The configuration file is stored in an S3 bucket.
Whenever relevant keywords are detected in the CloudTrail logs, the Lambda function posts a notification to an SNS topic.
SNS dispatches the notification to every topic subscriber via email, Amazon SQS, SMS, HTTP call, or mobile push.
Amazon CloudTrail Features
Always on
AWS CloudTrail is enabled on all AWS accounts and records your account activity upon account creation. You can view and download the last 90 days of your account activity for create, modify, and delete operations of supported services without the need to manually setup CloudTrail.
Event history
You can view, search, and download your recent AWS account activity.
Multi-region configuration
You can configure AWS CloudTrail to deliver log files from multiple regions to a single Amazon S3 bucket for a single account.
Log file integrity validation
You can validate the integrity of AWS CloudTrail log files stored in your Amazon S3 bucket and detect whether the log files were unchanged, modified, or deleted.
Log file encryption
By default, AWS CloudTrail encrypts all log files delivered to your specified Amazon S3 bucket using Amazon S3 server-side encryption (SSE).
Management events
Management events provide insights into the management (“control plane”) operations performed on resources in your AWS account..
Integrations
AWS Lambda
You can take advantage of the Amazon S3 bucket notification feature to direct Amazon S3 to publish object-created events to AWS Lambda. When CloudTrail writes logs to your S3 bucket, Amazon S3 can invoke your Lambda function to process the access records logged by CloudTrail.
Amazon CloudWatch Logs
AWS CloudTrail integration with Amazon CloudWatch Logs enables you to send management and data events recorded by CloudTrail to CloudWatch Logs. CloudWatch Logs allows you to create metric filters to monitor events, search events, and stream events to other AWS services, such as AWS Lambda and Amazon Elasticsearch Service.
Amazon CloudWatch Events
AWS CloudTrail integration with Amazon CloudWatch Events enables you to automatically respond to changes to your AWS resources.
You can view, search, and download your recent AWS account activity.
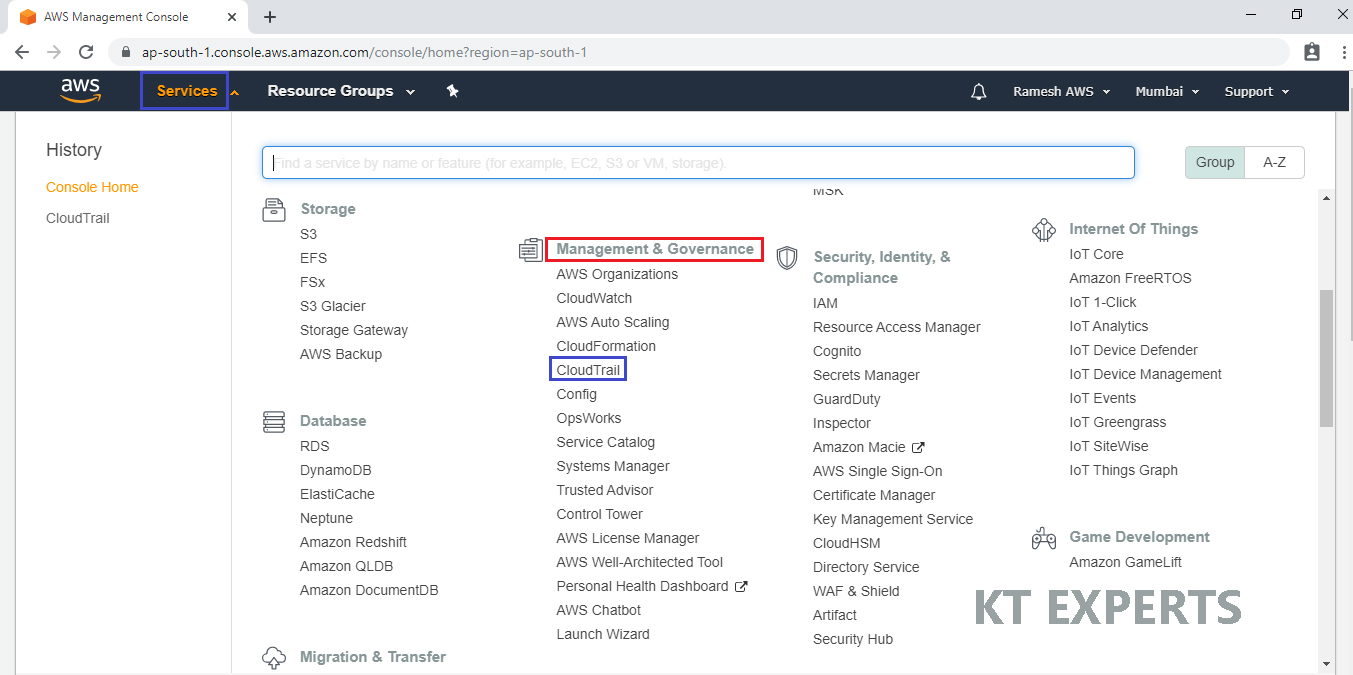
Go to Services, click on CloudTrail in the Management & Governance module.
You can view and search the last 90 days of events recorded by CloudTrail in the CloudTrail console
Go to Event history,
It will show every activity which is done in your AWS Account.
Cloud trail is enabled by default.
It is captured every activity in your AWS Account.
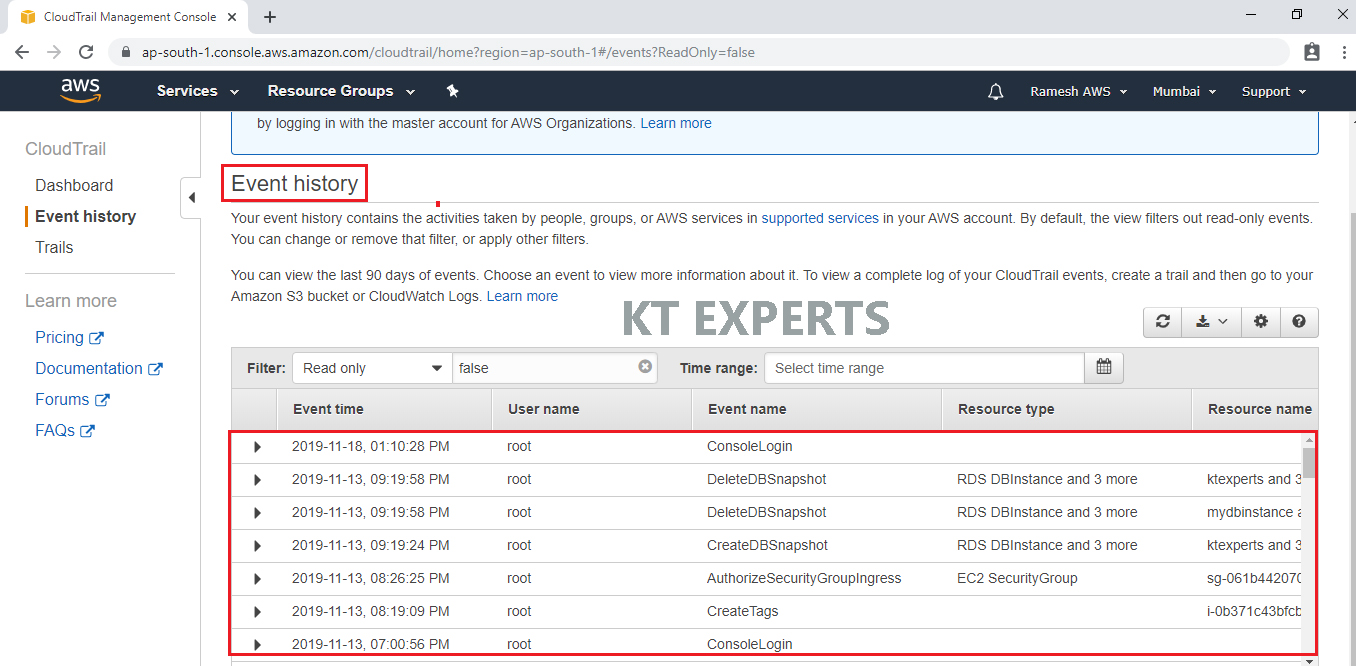
To see more information about an event, expand it.

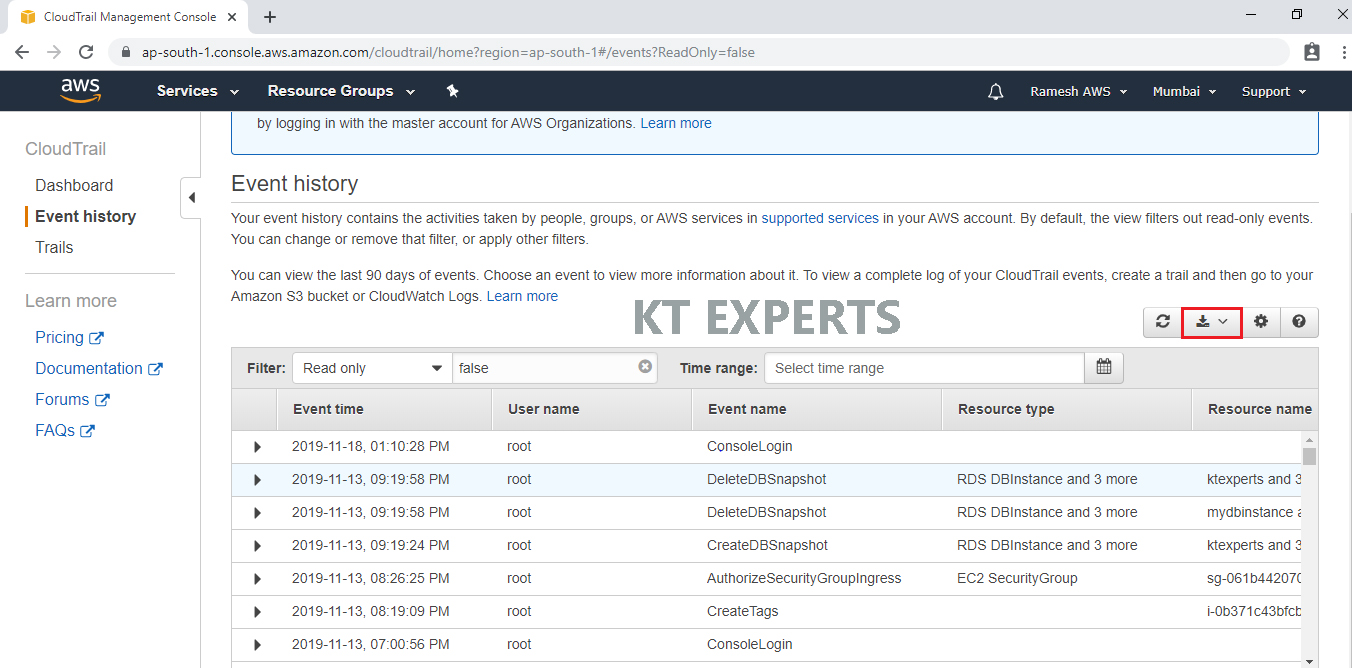
Download Event History
We can download a CSV or JSON file containing up to the past 90 days of CloudTrail events
In the Event history, click on Download Button at the top corner of the page.
We can see the downloaded event history excel file in the physical location.
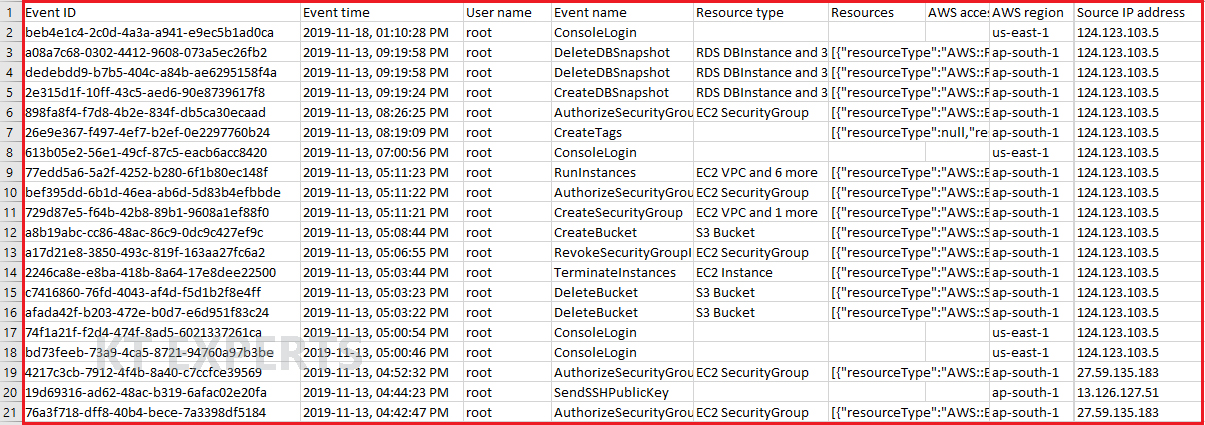
Once open event history excel file,we can see cloud trail log files that belongs to every activity which has done in your AWS account.
Thank you for giving your valuable time to read the above information. Please click here to subscribe for further updates
KTEXPERTS is always active on below social media platforms.
Facebook : https://www.facebook.com/ktexperts/
LinkedIn : https://www.linkedin.com/company/ktexperts/
Twitter : https://twitter.com/ktexpertsadmin
YouTube : https://www.youtube.com/c/ktexperts
Instagram : https://www.instagram.com/knowledgesharingplatform