Dear Readers,
In this article,we will see Create Custom/Public Network ACL in VPC and Connect to Database Server through Bastion Server.

Implementation Steps
- Create Public Network ACL.
- Connect Public Network ACL “Network ACL – Public” to subnet 1 “192.168.2.0/24 – ap-south-1a (subnet-1) – (Public Subnet).
- Configure Inbound Rules for Public Network ACL “Network ACL – Public”.
- Verify WebServer.
- Configure Outbound Rules for Public Network ACL “Network ACL – Public”.
- Verify Web Server.
- Go to Bastion Server linux terminal and connect to DBServer then Install MySQL package.
Create Public Network ACL
Go to Network ACLs,Click on Create network ACL.
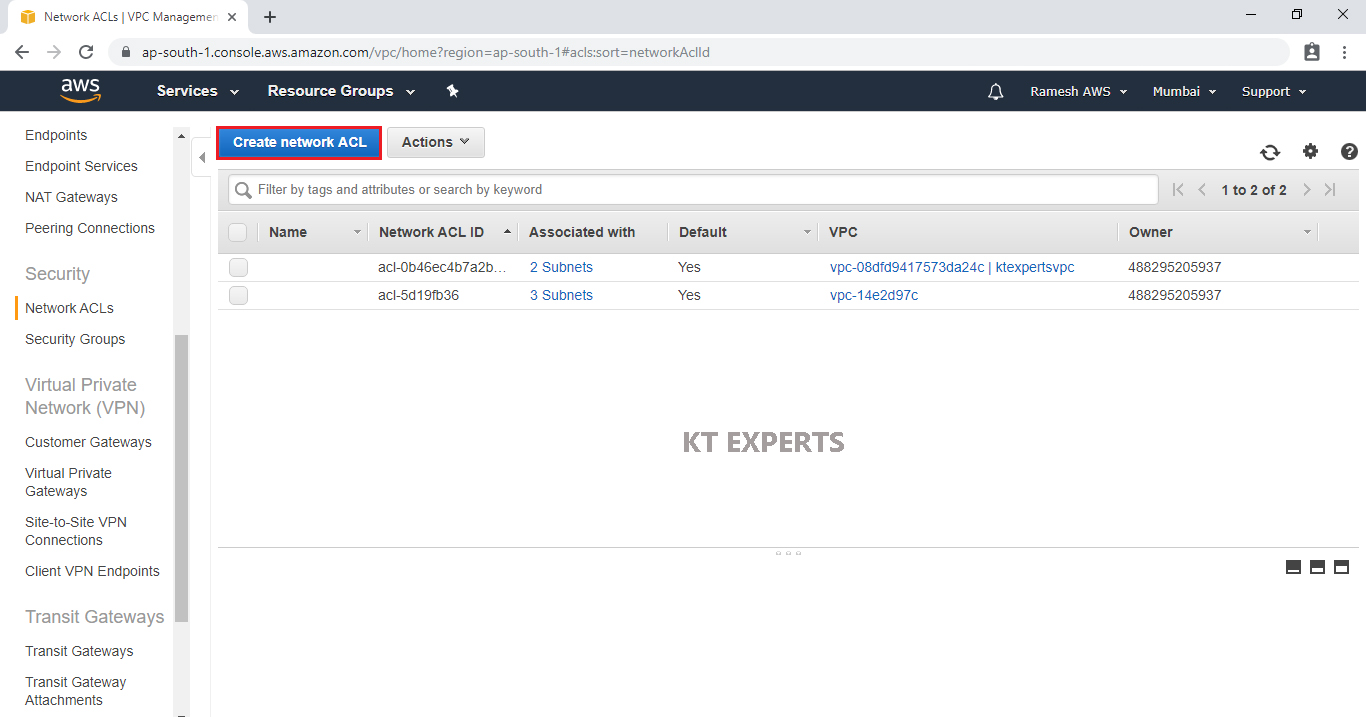
Specify Name tag “Network ACL – Public” for network ACL.
Choose your vpc from list and click on create.
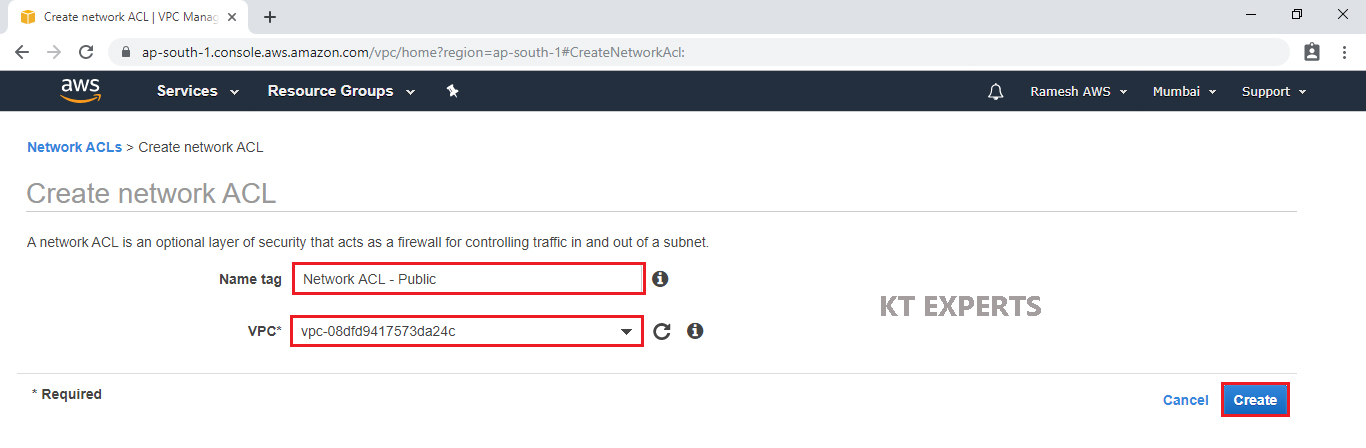
The Public Network ACL has been created successfully.
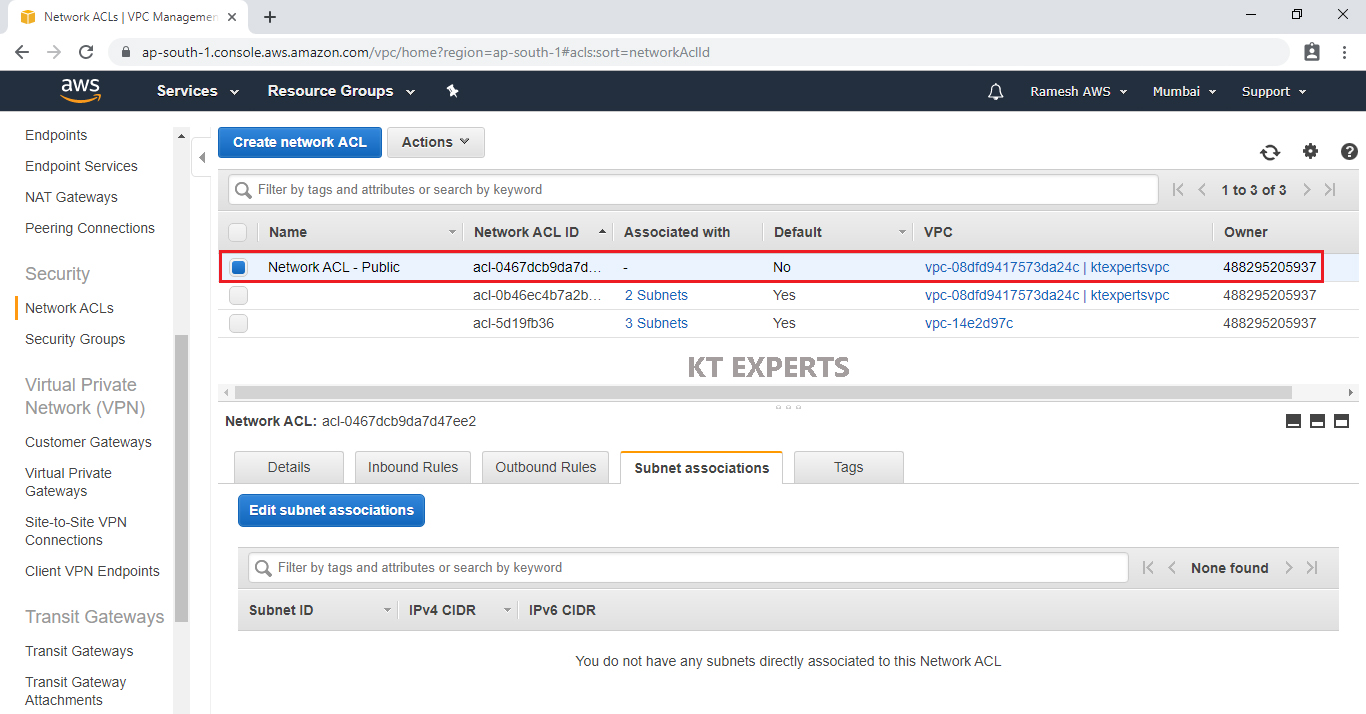
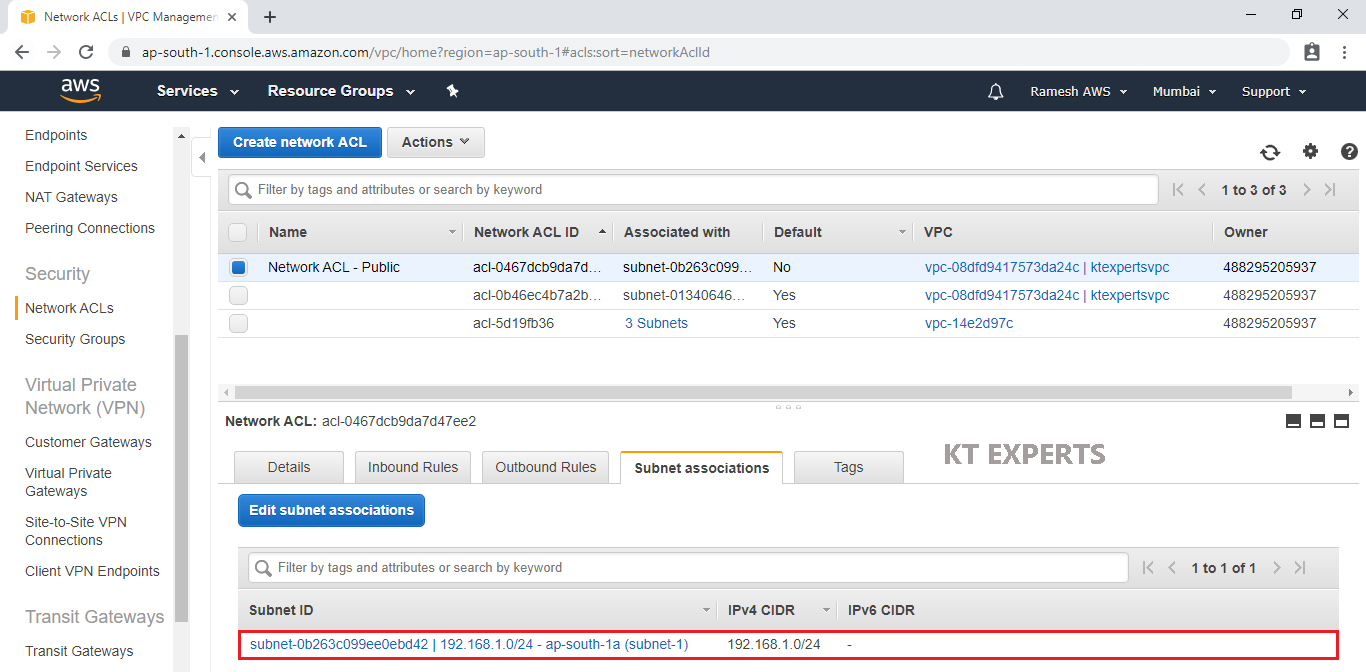
Connect Public Network ACL “Network ACL – Public” to subnet 1 “192.168.2.0/24 – ap-south-1a (subnet-1) – (Public Subnet)
Select Public Network ACL “Network ACL – Public” and go to subnet Associations then click on Edit subnet associations.
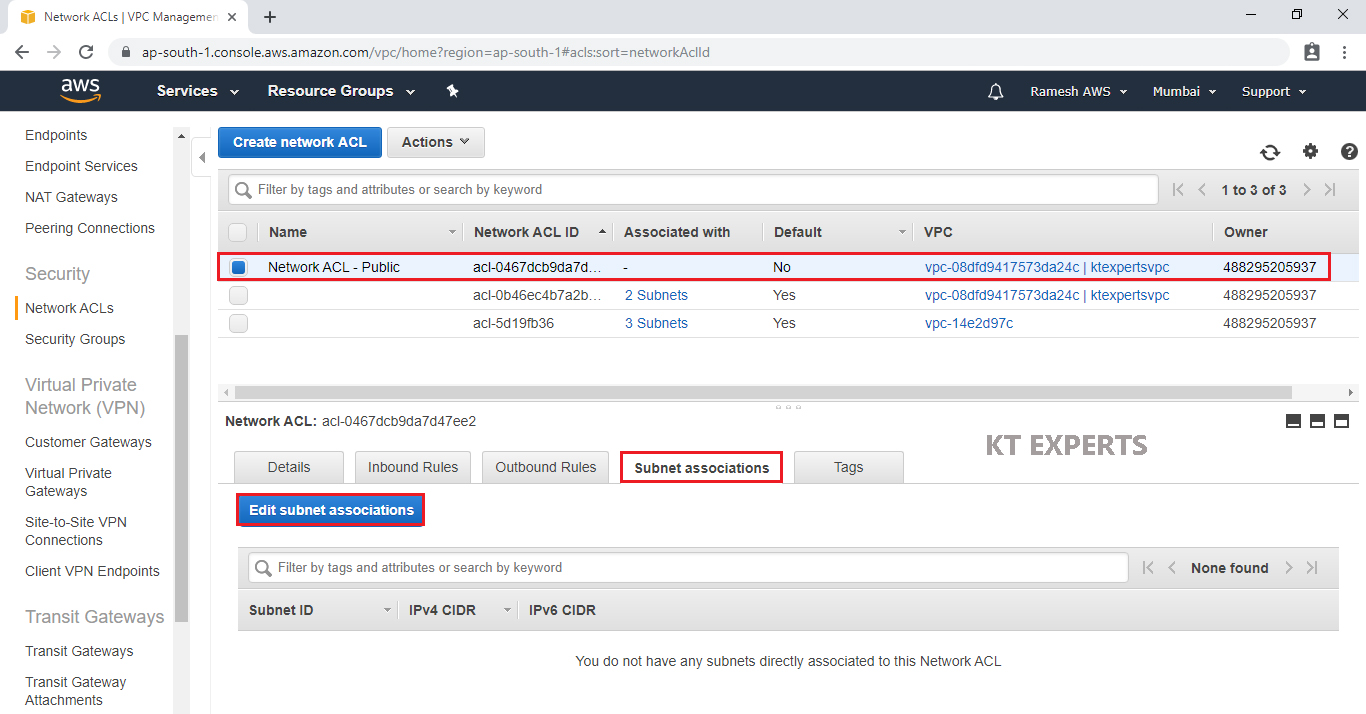
Checked subnet 1 ID “192.168.2.0/24 – ap-south-1a (subnet-1)” and click on Edit.
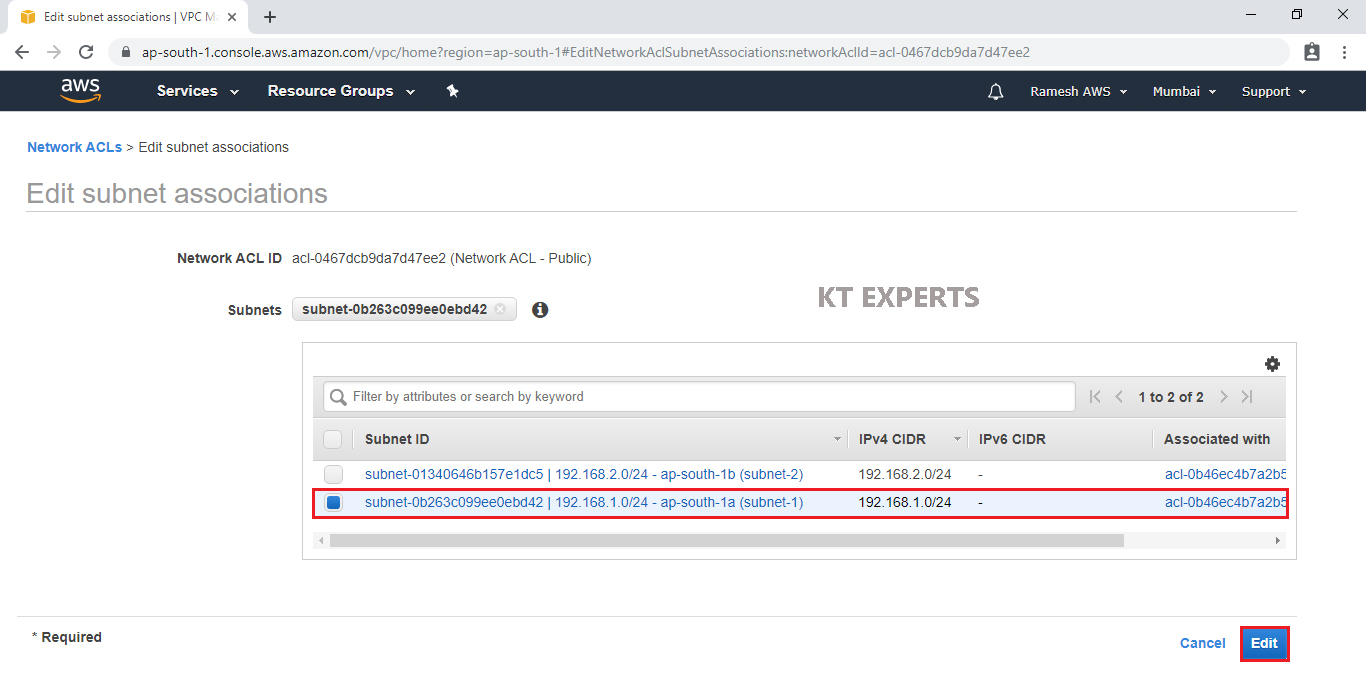
We can see the Public Network ACL “Network ACL – Public” has been connected to subnet 1 “192.168.1.0/24 – ap-south-1a (subnet-1) – (Public Subnet).
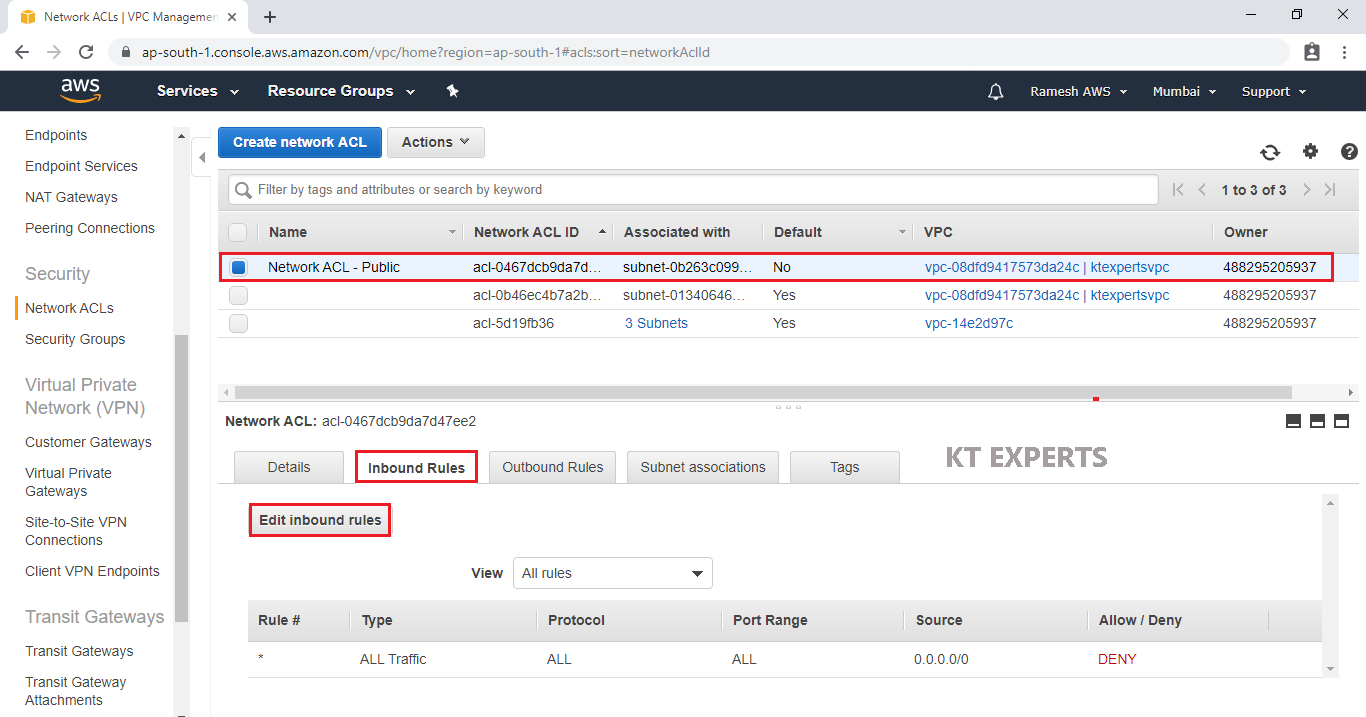
Configure Inbound Rules for Public Network ACL “Network ACL – Public”
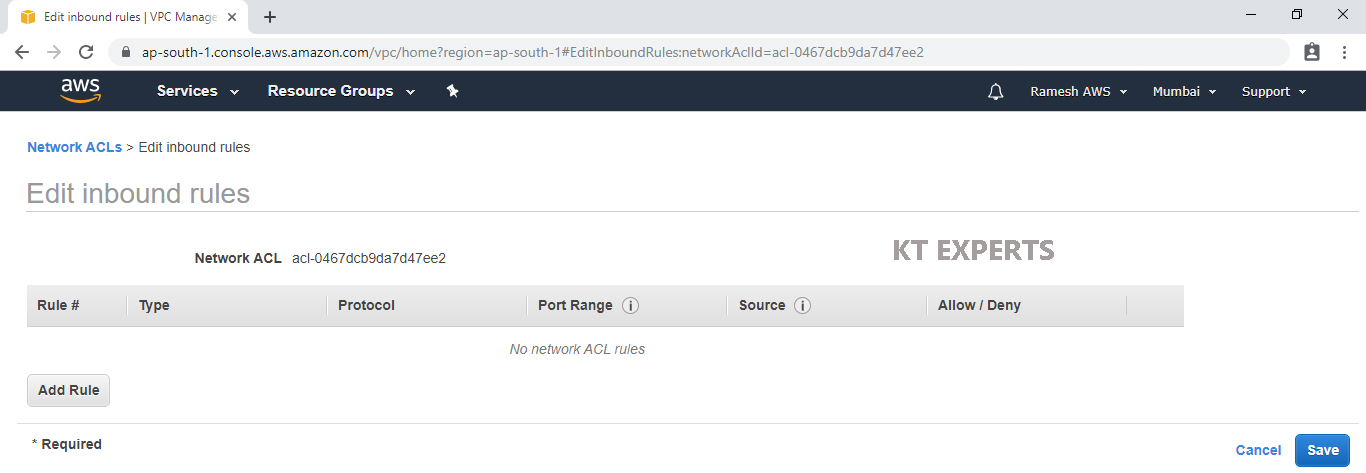
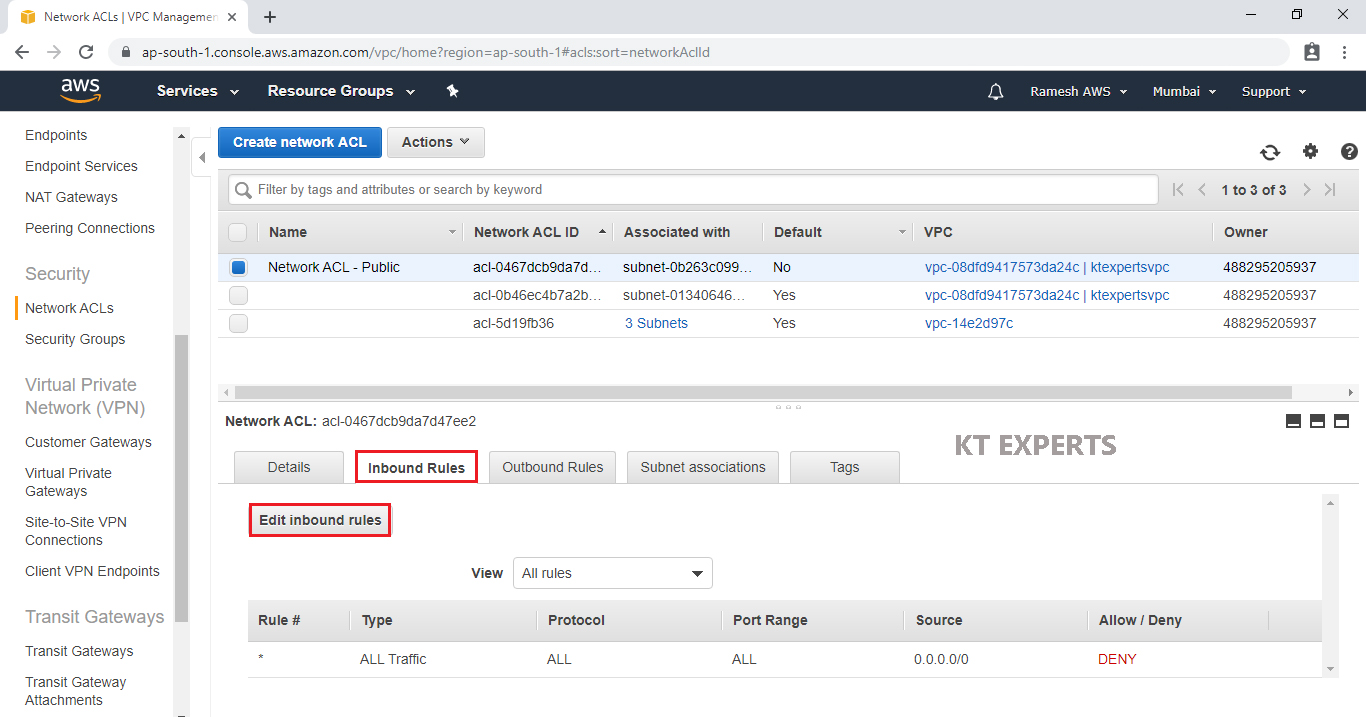
Select Public Network ACL “Network ACL – Public” and go to inbound Rules then click on Edit inbound rules.
Copy My IP
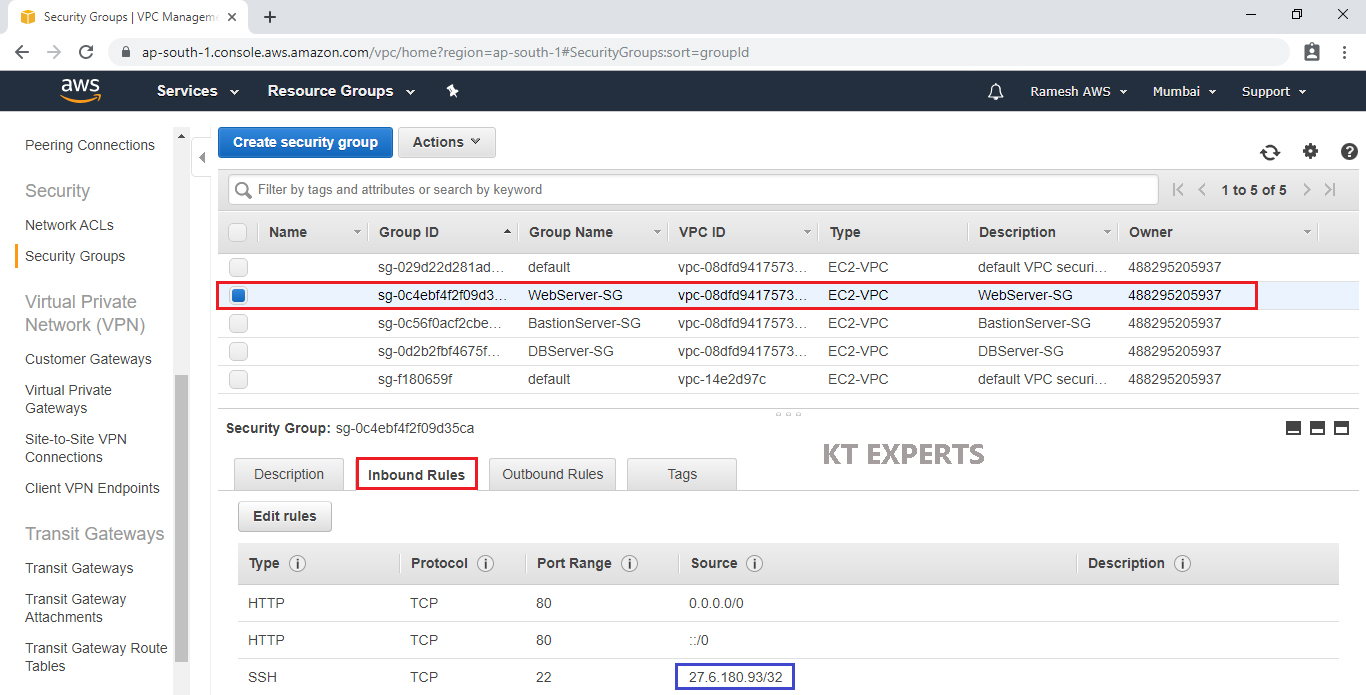
Go to Security Groups , Select WebServer Security Group “WebServer-SG”
Copy SSH source IP I the inbound Rules
Note
We configured SSH port – open to My IP (27.6.180.93/32).
Select Public Network ACL “Network ACL – Public” and go to inbound Rules then click on Edit inbound rules.
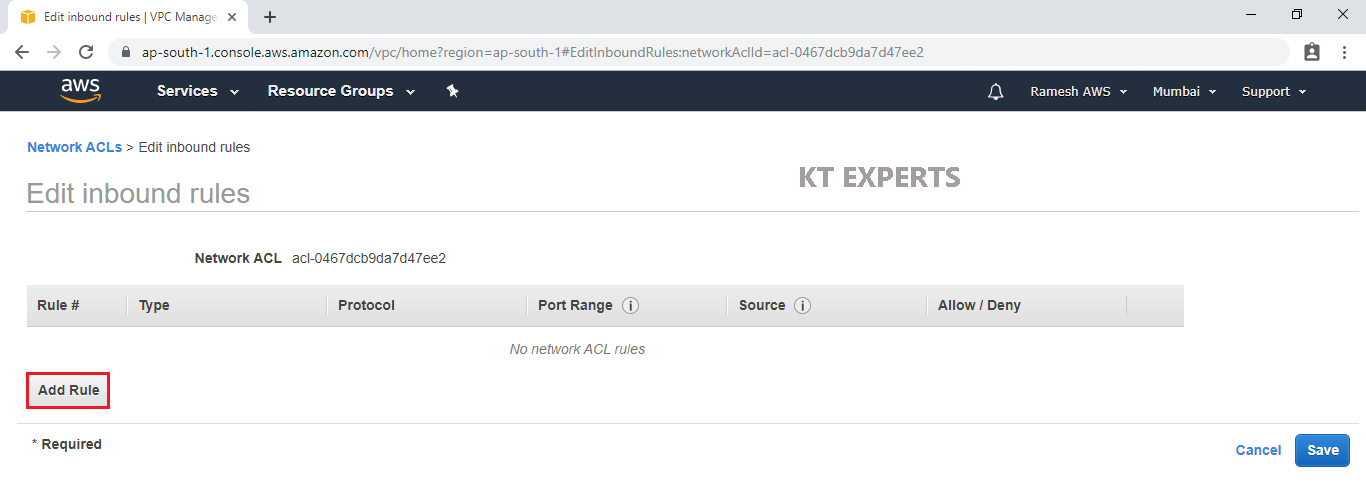
Click on Add Rule.
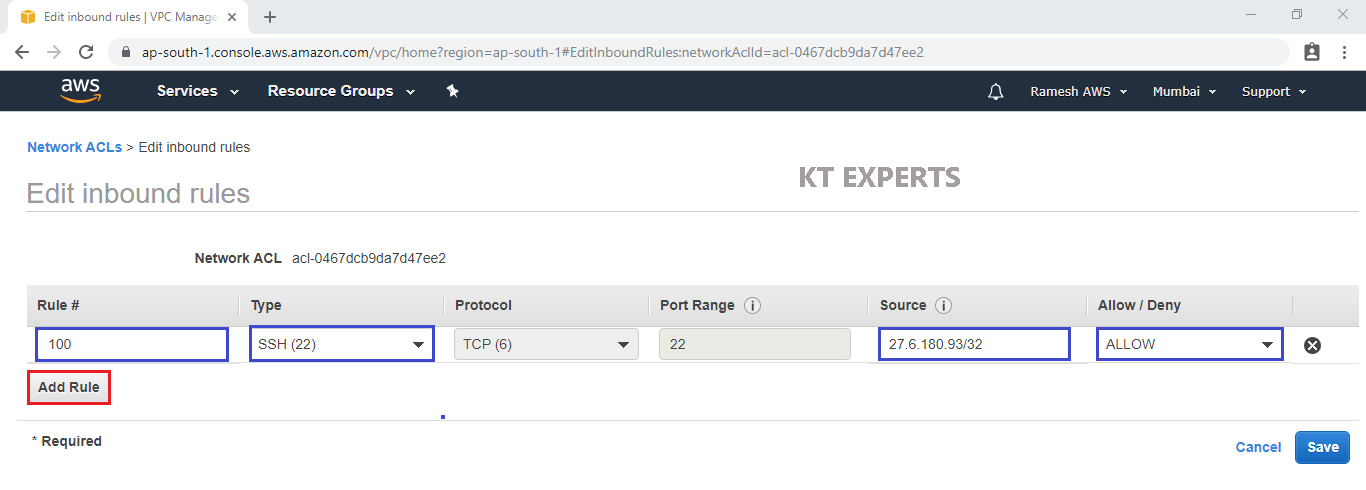
Add SSH Port
We need to specify Rule,Type,Source.
Rule – 100
Type – SSH
Source – 27.6.180.93/32 (My IP) (which was copied earlier)
Click on Add Rule.
Add HTTP Port
Rule – 200
Type – HTTP
Source – 0.0.0.0/0 (Anywhere) and allow the port.
Click on Add Rule.
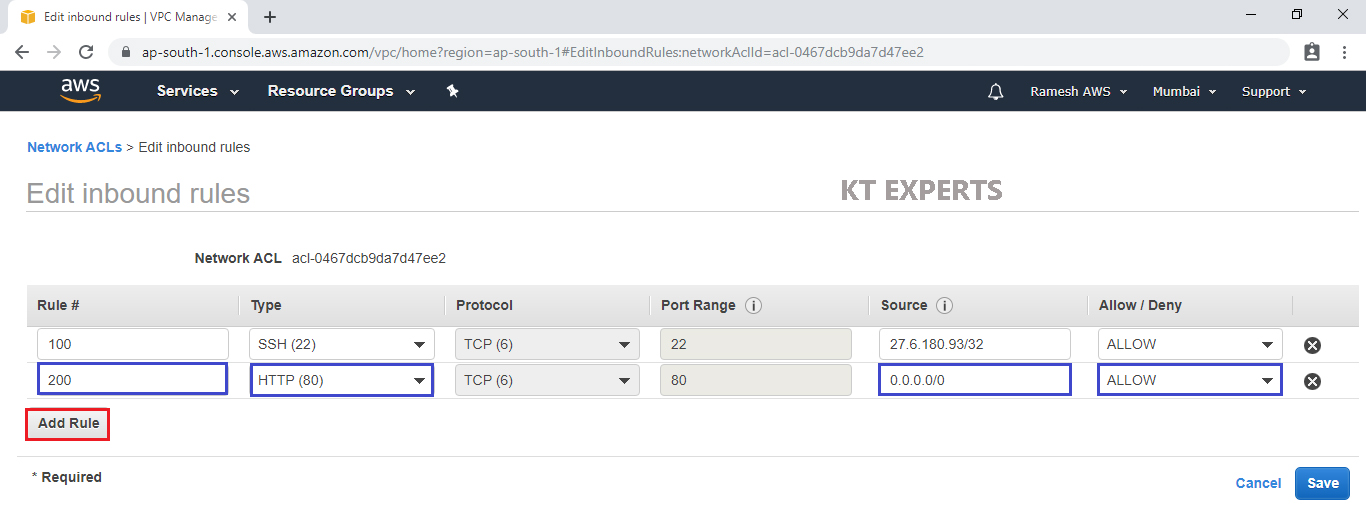
Add Custom TCP Rule
Rule – 300
Type – Custom TCP Rule
Source – 0.0.0.0/0 (Anywhere) and allow the port.
Click on Save.
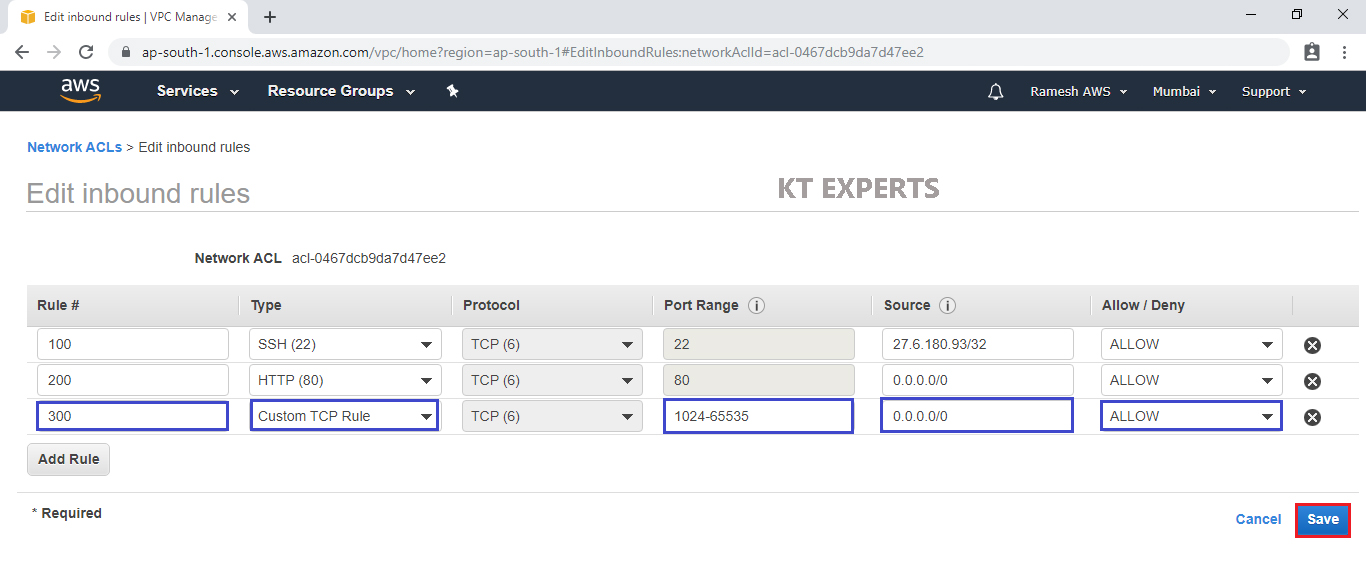
The Inbound Rules has been configured successfully.
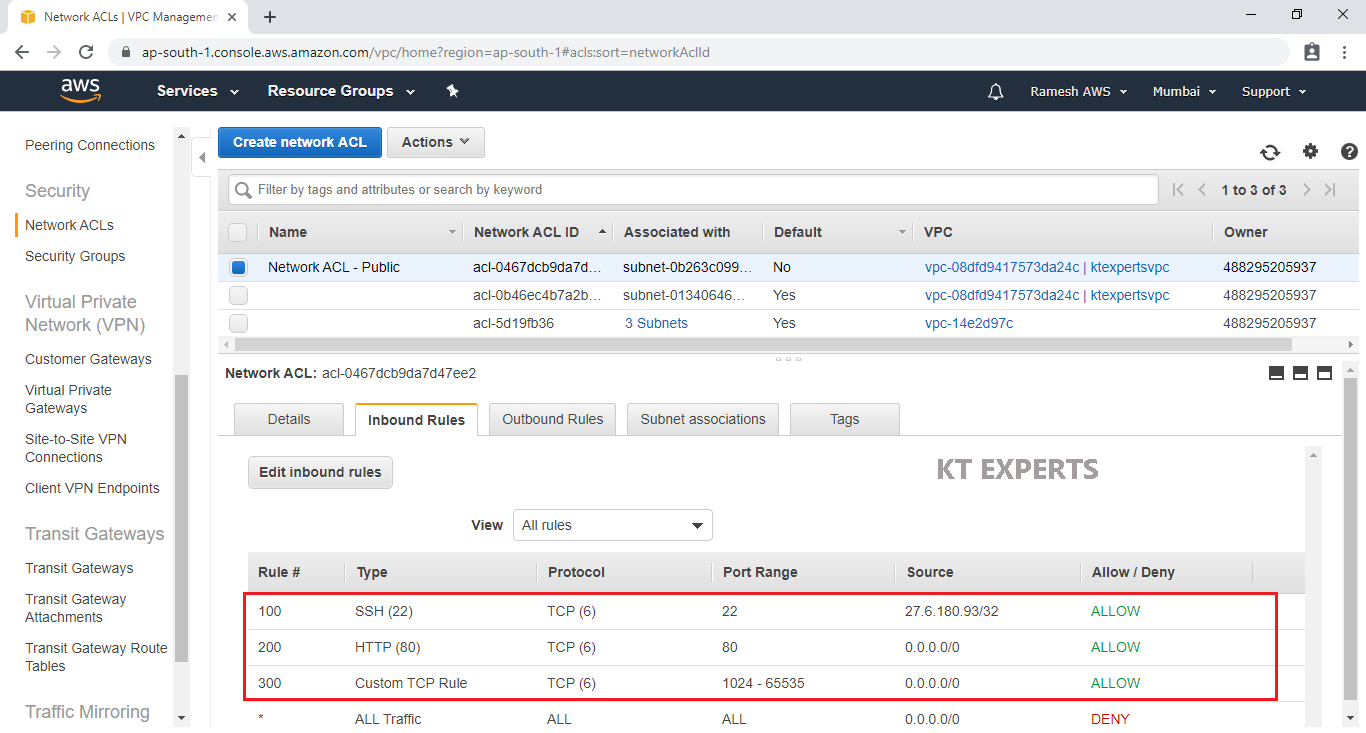
Note
Whatever the ports configured in WebServer SG we need to configure in Public Network ACL inbound rules.
We need to configure one additional rule i.e., Custom TCP Rule.
Verify WebServer
Select WebServer and copy Public IP of the WebServer.
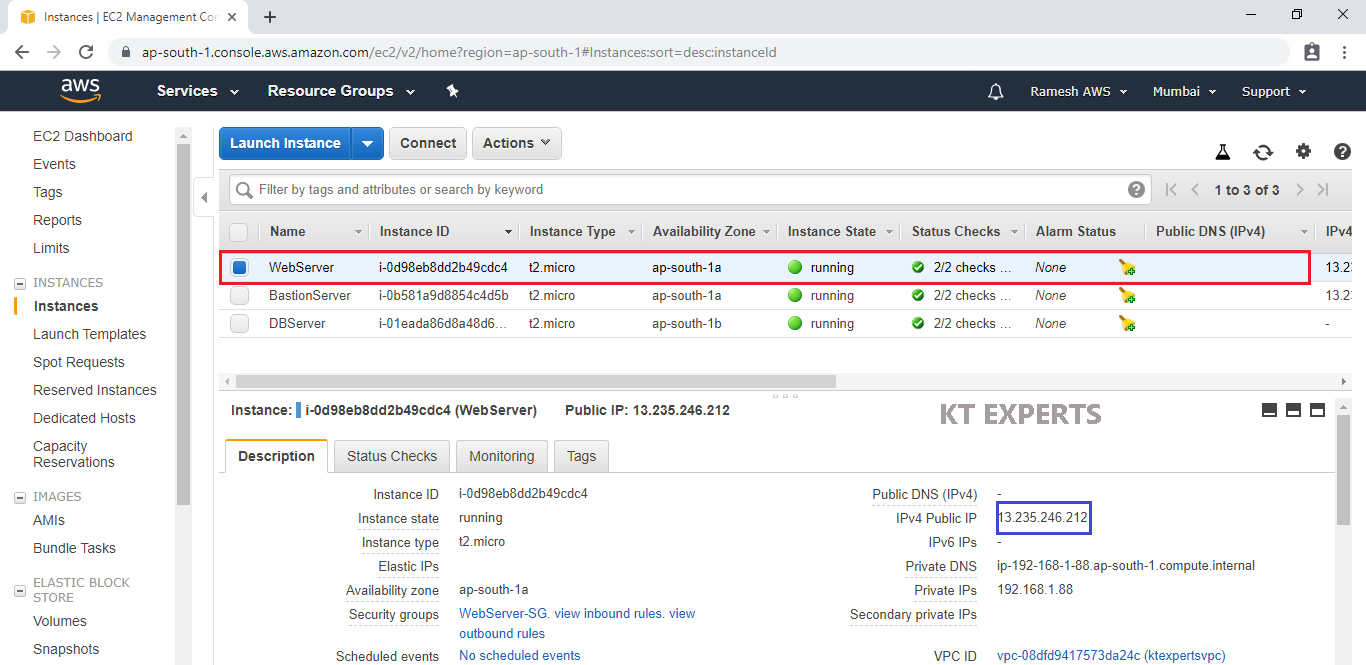
Search Web Server Public IP in browser
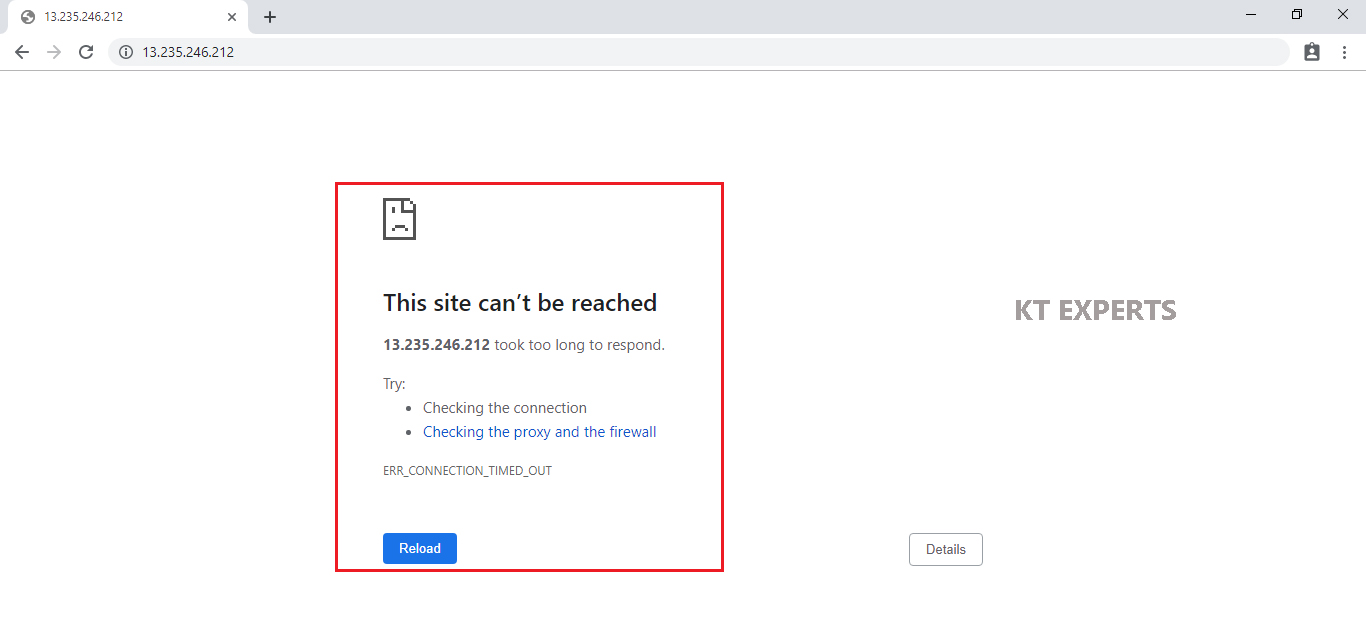
We are unable to see the content of the WebServer
Note
We didn’t configure the outbound Rules
In the Network ACL we need to configure both inbound and outbound Rules then only we can able to see the content of the WebServer
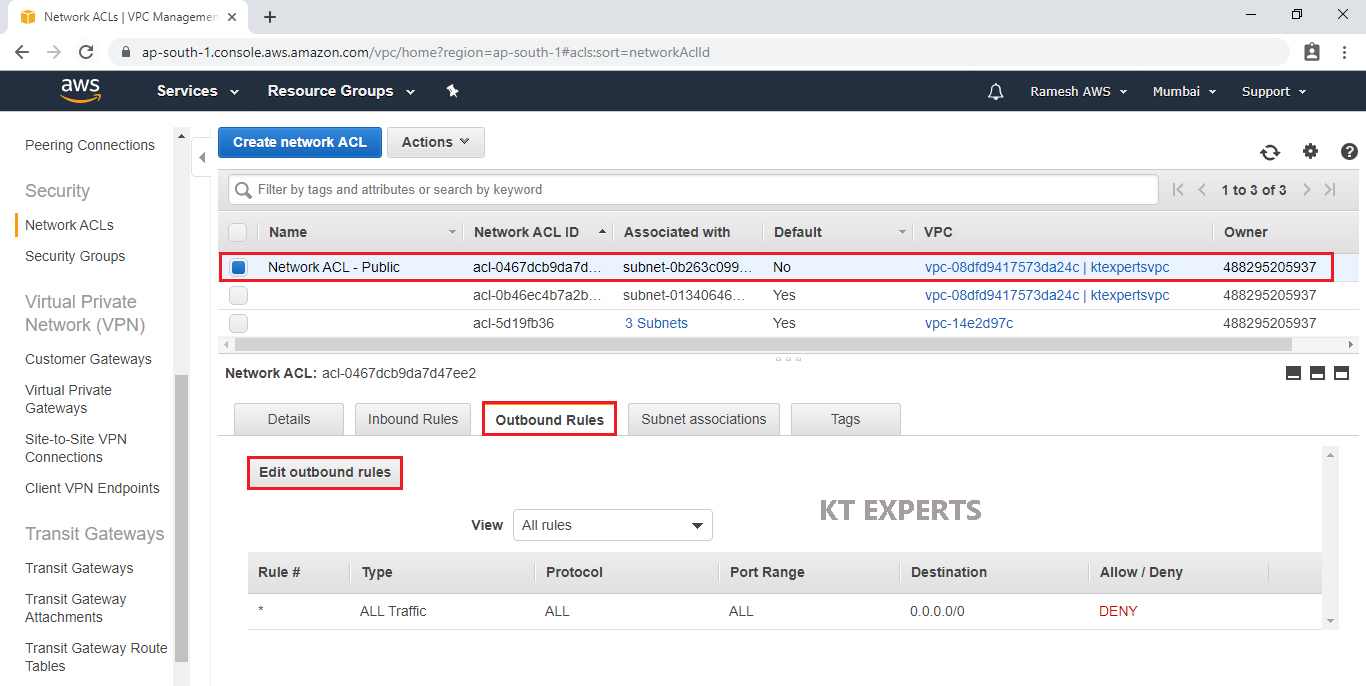
Configure Outbound Rules for Public Network ACL “Network ACL – Public”
Select Public Network ACL “Network ACL – Public” and go to outbound Rules then click on Edit outbound rules.
Click on Add Rule.
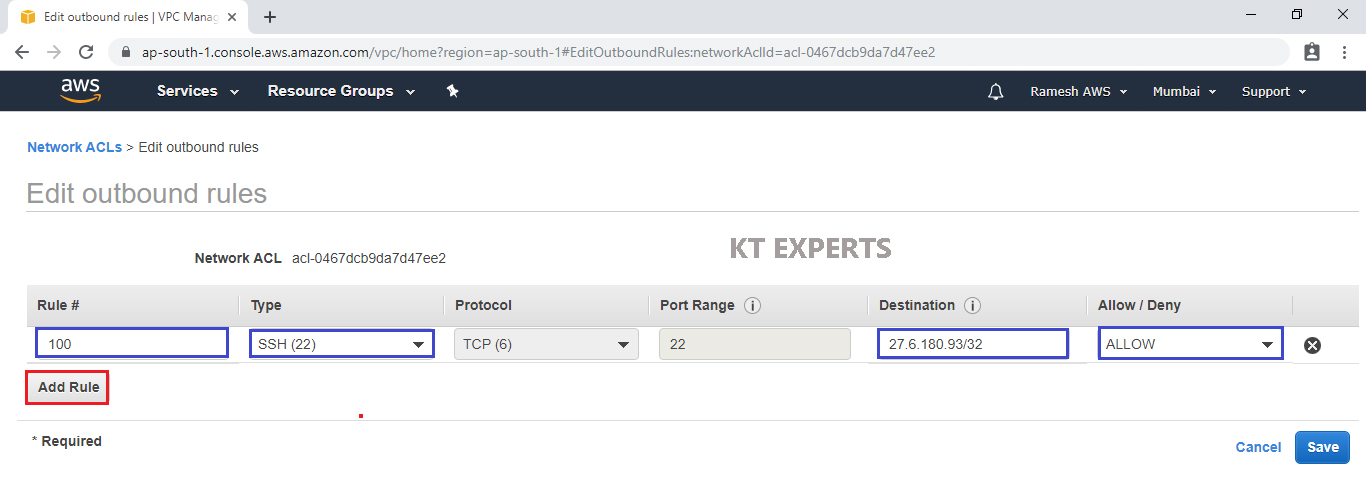
Add SSH Port
We need to specify Rule,Type,Source.
Rule – 100
Type – SSH
Source – 27.6.180.93/32 (My IP) (which was copied earlier)
Click on Add Rule.
Add HTTP Port
Rule – 200
Type – HTTP
Source – 0.0.0.0/0 (Anywhere) and allow the port.
Click on Add Rule.
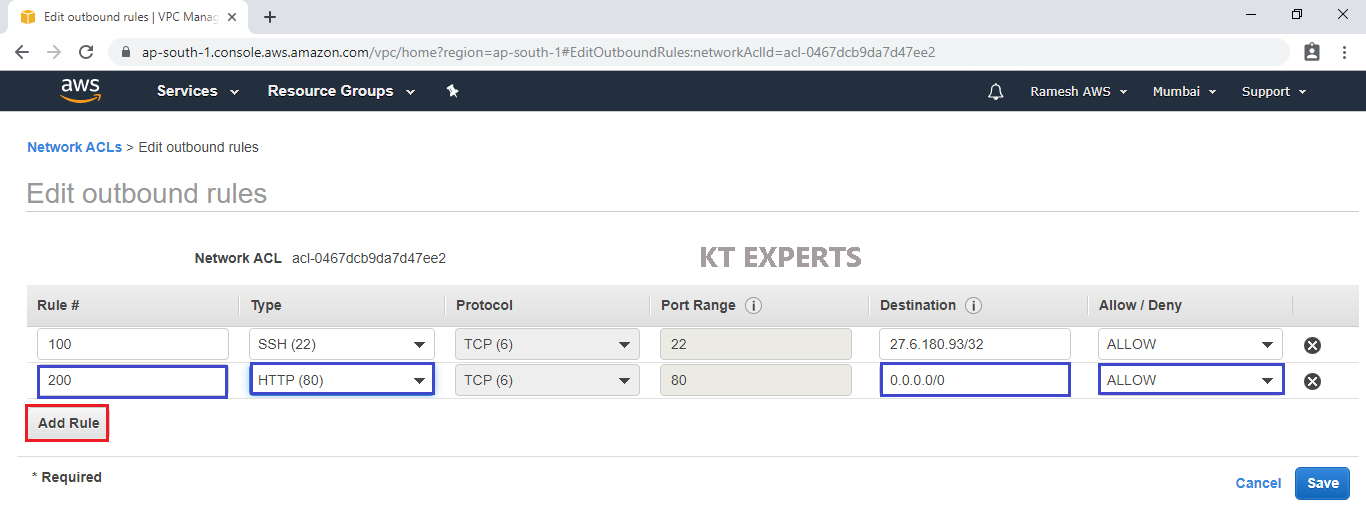
Add Custom TCP Rule
Rule – 300
Type – Custom TCP Rule
Source – 0.0.0.0/0 (Anywhere) and allow the port.
Click on Save.
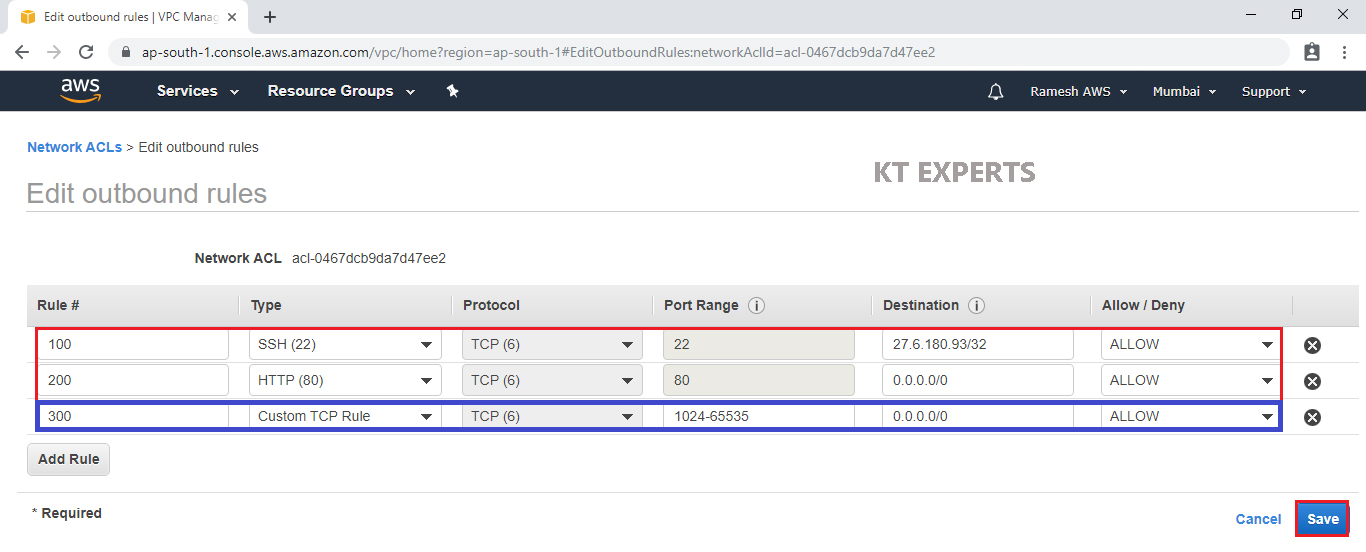
The outbound rules has been configured successfully.
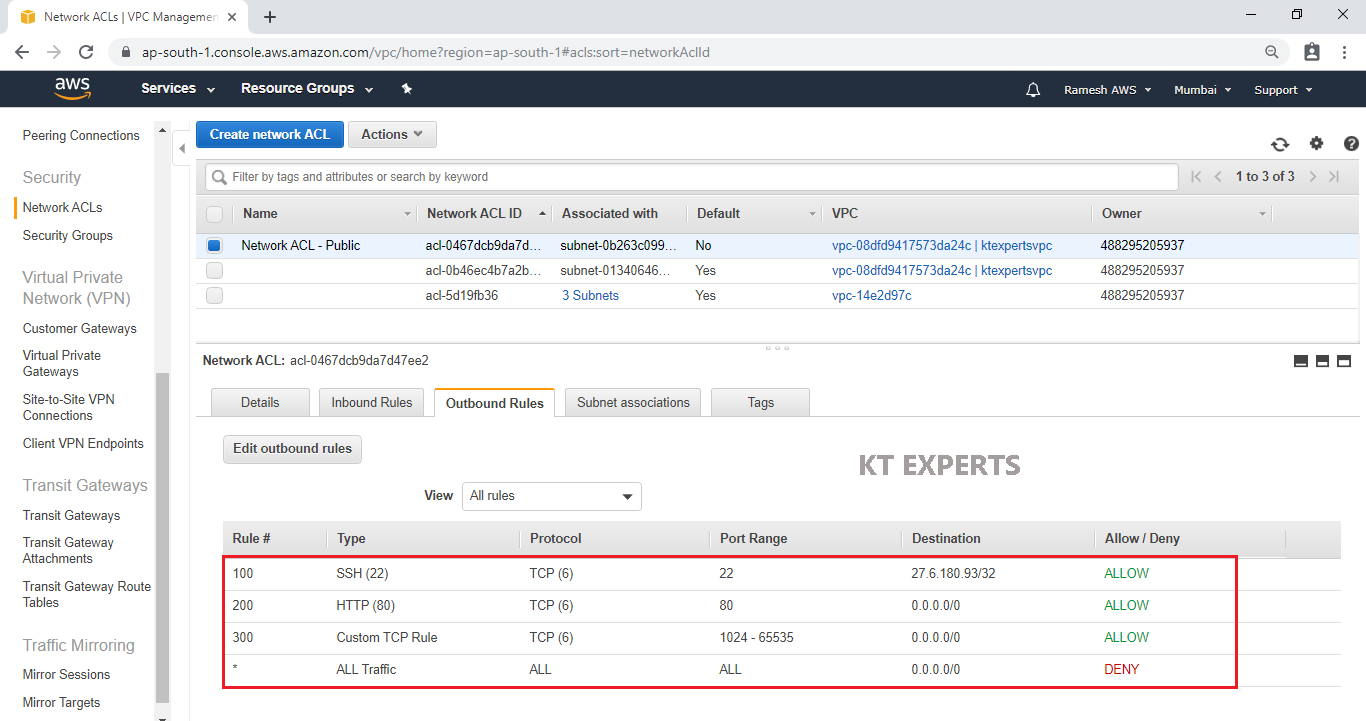
Verify Web Server
Search Web Server Public IP in browser
Refresh public IP of web server.
We are able to see the content because we Configured both inbound and outbound rules.
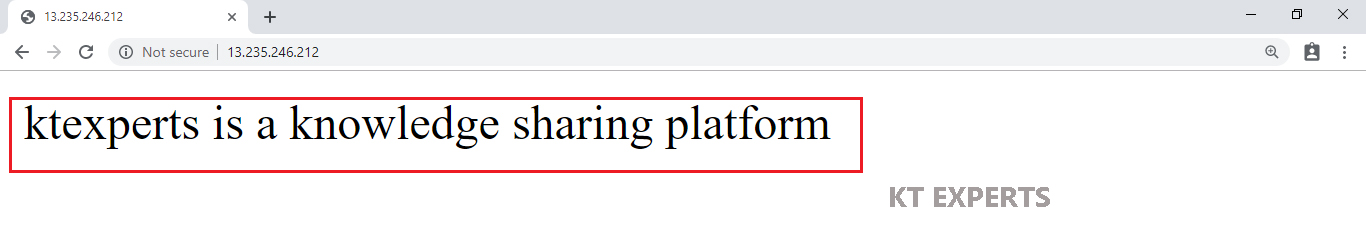
Go to Bastion Server linux terminal and connect to DBServer then Install MySQL package
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 |
Using username "ec2-user". Authenticating with public key "imported-openssh-key" Last login: Sat Sep 21 05:19:11 2019 from 124.123.103.5 __| __|_ ) _| ( / Amazon Linux 2 AMI ___|\___|___| https://aws.amazon.com/amazon-linux-2/ 7 package(s) needed for security, out of 10 available Run "sudo yum update" to apply all updates. [ec2-user@ip-192-168-1-143 ~]$ |
Switch to root user
|
1 2 3 4 |
[ec2-user@ip-192-168-1-143 ~]$ sudo su [root@ip-192-168-1-143 ec2-user]# |
Verify Database pem file
|
1 2 3 4 |
[root@ip-192-168-1-143 ec2-user]# ls dbserver.pem |
Connect to Database Server
|
1 2 3 4 5 6 7 8 9 10 11 12 |
[root@ip-192-168-1-143 ec2-user]# ssh -i "dbserver.pem" ec2-user@192.168.2.85 Last login: Sat Sep 21 05:20:10 2019 from 192.168.1.143 __| __|_ ) _| ( / Amazon Linux 2 AMI ___|\___|___| https://aws.amazon.com/amazon-linux-2/ |
Switch to root user
|
1 2 3 4 |
[ec2-user@ip-192-168-2-85 ~]$ sudo su [root@ip-192-168-2-85 ec2-user]# |
Install mysql package
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 |
[root@ip-172-31-34-108 ec2-user]# yum install mysql -y Loaded plugins: extras_suggestions, langpacks, priorities, update-motd amzn2-core | 2.4 kB 00:00 amzn2extra-docker | 1.3 kB 00:00 Resolving Dependencies --> Running transaction check ---> Package mariadb.x86_64 1:5.5.64-1.amzn2 will be installed --> Finished Dependency Resolution Dependencies Resolved ================================================================================ Package Arch Version Repository Size ================================================================================ Installing: mariadb x86_64 1:5.5.64-1.amzn2 amzn2-core 9.0 M Transaction Summary ================================================================================ Install 1 Package Total download size: 9.0 M Installed size: 49 M Downloading packages: mariadb-5.5.64-1.amzn2.x86_64.rpm | 9.0 MB 00:00 Running transaction check Running transaction test Transaction test succeeded Running transaction Installing : 1:mariadb-5.5.64-1.amzn2.x86_64 1/1 Verifying : 1:mariadb-5.5.64-1.amzn2.x86_64 1/1 Installed: mariadb.x86_64 1:5.5.64-1.amzn2 Complete! |
Thank you for giving your valuable time to read the above information. Please click here to subscribe for further updates
KTEXPERTS is always active on below social media platforms.
Facebook : https://www.facebook.com/ktexperts/
LinkedIn : https://www.linkedin.com/company/ktexperts/
Twitter : https://twitter.com/ktexpertsadmin
YouTube : https://www.youtube.com/c/ktexperts
Instagram : https://www.instagram.com/knowledgesharingplatform





Veeranjaneyulu
This is good information and useful to everyone