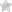Dear Readers,
In this article, we will see the Amazon VPC Network ACL in AWS.

Network ACL (NACL)
NACL stands for Network Access Control Lists.
It is an optional layer of security for your VPC
NACL acts as a firewall for controlling traffic in and out of one or more subnets.
You might set up network ACLs with rules similar to your security groups in order to add an additional layer of security to your VPC.
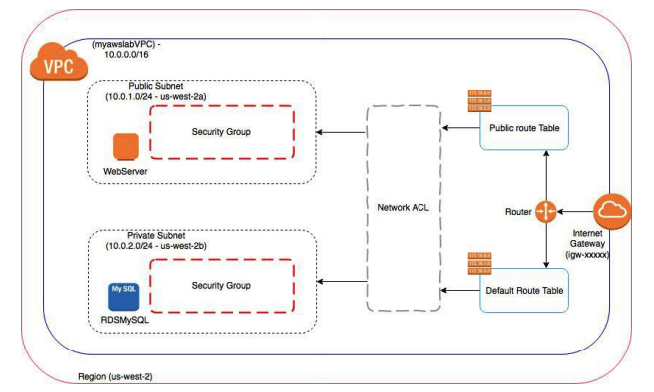
Difference between Security Group and Network ACL
Network ACL Basics
The following are the basic things that you need to know about network ACLs:
Your VPC automatically comes with a modifiable default network ACL.
By default, it allows all inbound and outbound IPv4 traffic and, if applicable, IPv6 traffic.
You can create a custom network ACL and associate it with a subnet.
By default, each custom network ACL denies all inbound and outbound traffic until you add rules.
Each subnet in your VPC must be associated with a network ACL.
If you don’t explicitly associate a subnet with a network ACL, the subnet is automatically associated with the default network ACL.
You can associate a network ACL with multiple subnets;
A subnet can be associated with only one network ACL at a time..
A network ACL contains a numbered list of rules that we evaluate in order, starting with the lowest numbered rule, to determine whether traffic is allowed in or out of any subnet associated with the network ACL.
The highest number that you can use for a rule is 32766. We recommend that you start by creating rules in increments (for example, increments of 10 or 100)
A network ACL has separate inbound and outbound rules, and each rule can either allow or deny traffic.
Network ACLs are stateless.
This means any changes applied to an incoming rule will not be applied to the outgoing rule.
Example: If you allow an incoming port 80, you would also need to apply the rule for outgoing traffic.
Network ACL Rules
You can add or remove rules from the default network ACL, or create additional network ACLs for your VPC. When you add or remove rules from a network ACL, the changes are automatically applied to the subnets it’s associated with.
The following are the parts of a network ACL rule:
Rule number. Rules are evaluated starting with the lowest numbered rule. As soon as a rule matches traffic, it’s applied regardless of any higher-numbered rule that may contradict it.
Type. The type of traffic; for example, SSH. You can also specify all traffic or a custom range.
Protocol. You can specify any protocol that has a standard protocol number.
Port range. The listening port or port range for the traffic. For example, 80 for HTTP traffic.
Source. [Inbound rules only] The source of the traffic (CIDR range).
Destination. [Outbound rules only] The destination for the traffic (CIDR range).
Allow/Deny. Whether to ALLOW or DENY the specified traffic.
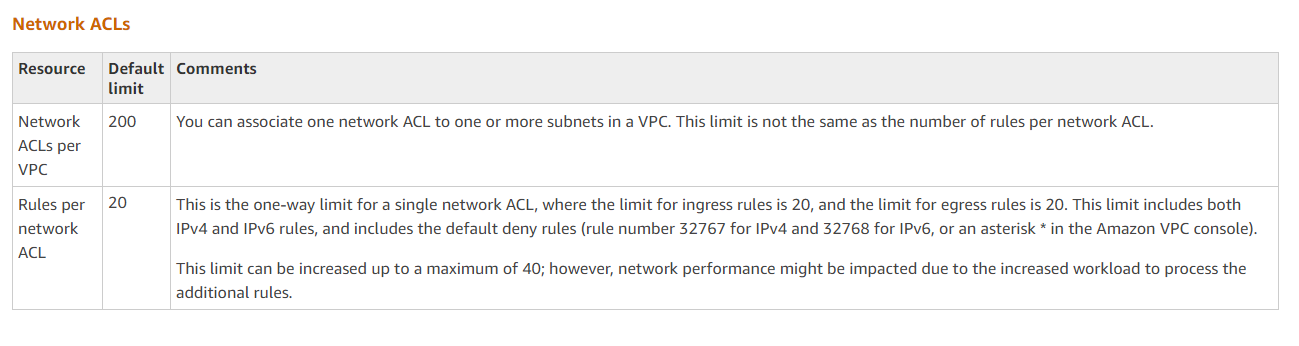
Network ACL Limits
Types of Network ACL
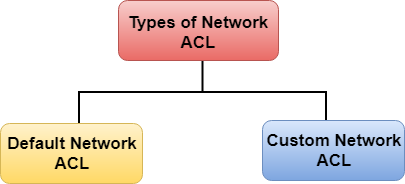
There are two types of Network ACL
- Default Network ACL
- Custom Network ACL
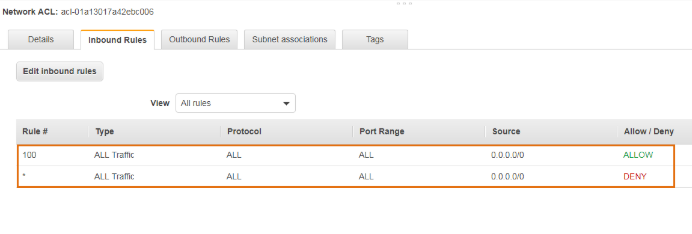
Default Network ACL
The default Network ACL allows all the traffic to flow in or out of the subnet which is associated with it. Each Network ACL also includes a rule whose rule number is asterisk which determines if traffic does not match any of the numbered rules, then it is denied. This rule cannot be modified or removed.
Inbound Rules
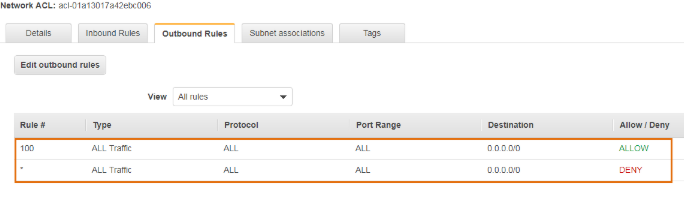
Outbound Rules
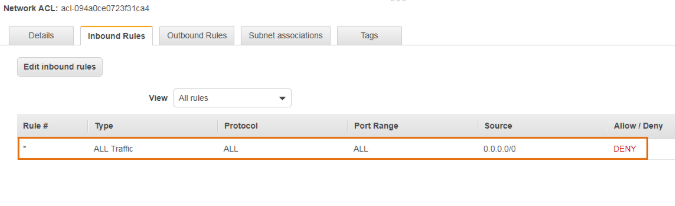
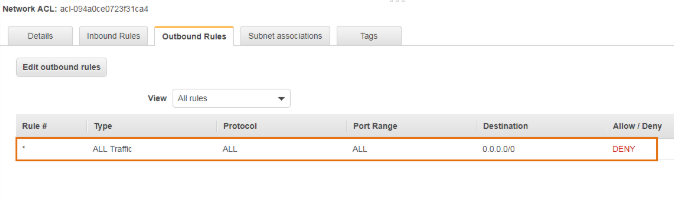
Custom Network ACL
Custom Network ACL is a user-defined Network ACL,By default, each custom network ACL denies all inbound and outbound traffic until you add rules.
Inbound Rules
Outbound Rules
Thank you for giving your valuable time to read the above information. Please click here to subscribe for further updates
KTEXPERTS is always active on below social media platforms.
Facebook : https://www.facebook.com/ktexperts/
LinkedIn : https://www.linkedin.com/company/ktexperts/
Twitter : https://twitter.com/ktexpertsadmin
YouTube : https://www.youtube.com/c/ktexperts
Instagram : https://www.instagram.com/knowledgesharingplatform