Dear Readers,
In this article, we will see the Prevent Deletion of Amazon S3 Bucket.
Realtime Usecase:
My Client need Common File Repository, everyone can access that File Repository.
But no one should delete that file repositoy,even storage Admins also.
Hint: Use Inline policy.

Steps to Follow
- Logging to AWS Account
- Create Group “Storage-Admin”
- Create Users “S3-User1 &S3-User2” and add to group “Storage-Admin”
- Create S3 Buckets “ktexpertsbucket-1 & ktexpertsbucket-2”
- Add Inline Policy to Group
- Logging to User “S3-User1” and Delete the First Bucket “ktexpertsbucket-1”
1. Logging to AWS Account
First, we need to AWS Console page by using below link.
https://aws.amazon.com/console/
Click on sign in to Console button.
Provide username and password then click on sign in.
Enter to AWS Management Console
We can see the AWS Management Console Dashboard.
2. Create Group “Storage-Admin”
Go to Security, Identity & compliance module click on IAM service to open.
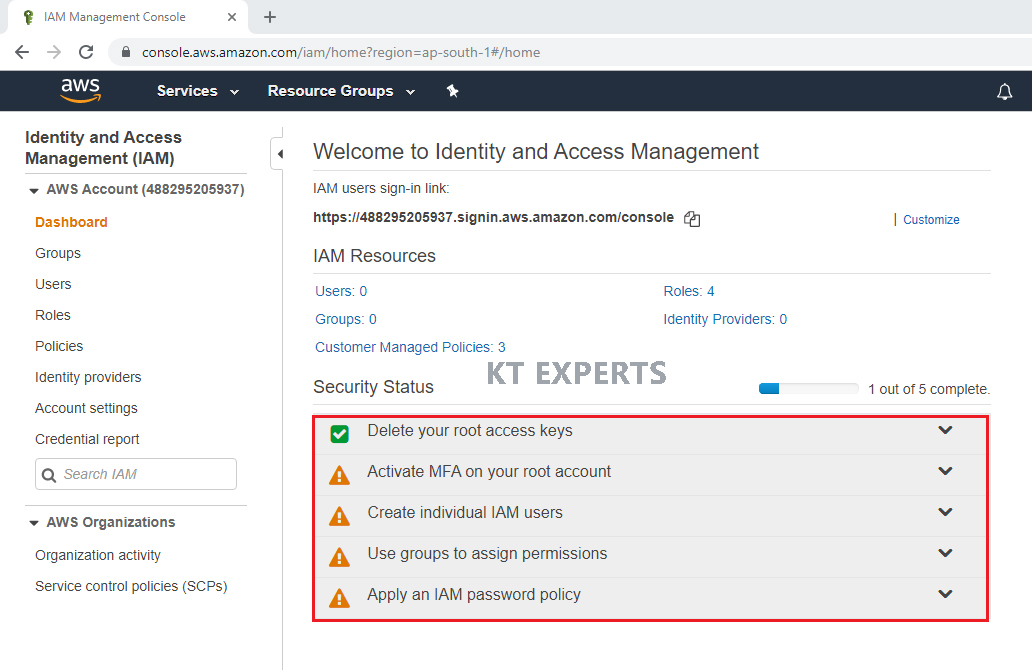
We can see IAM Management Dashboard.
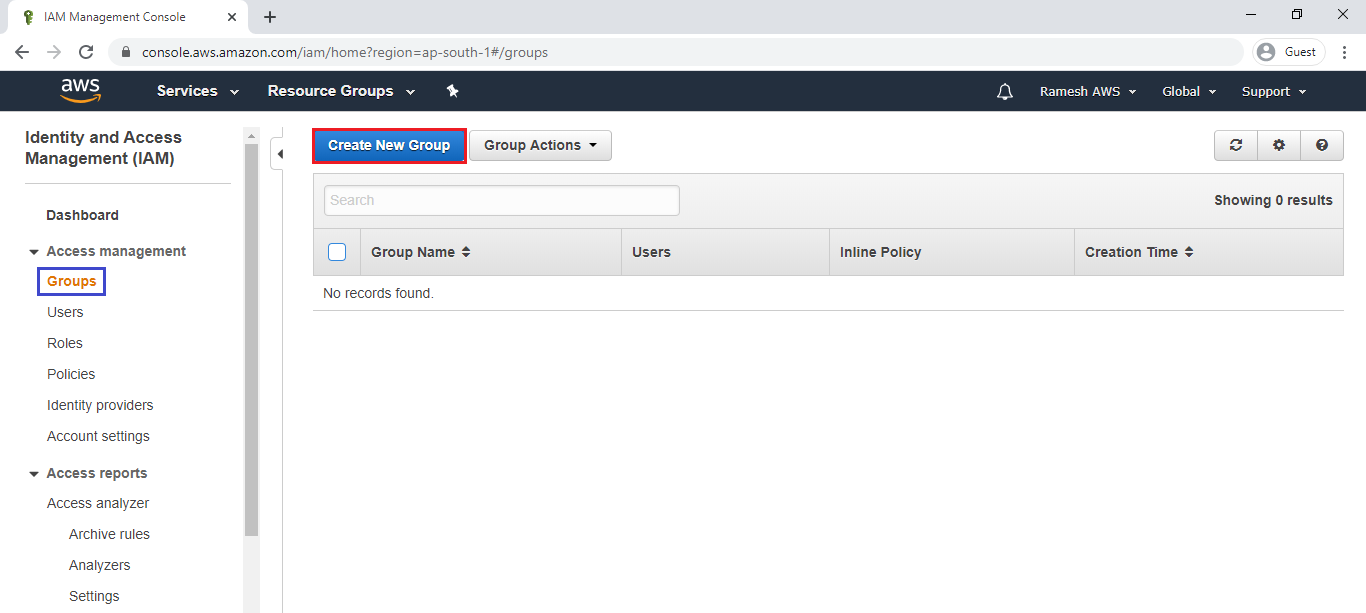
Go groups and click on groups to create new group.
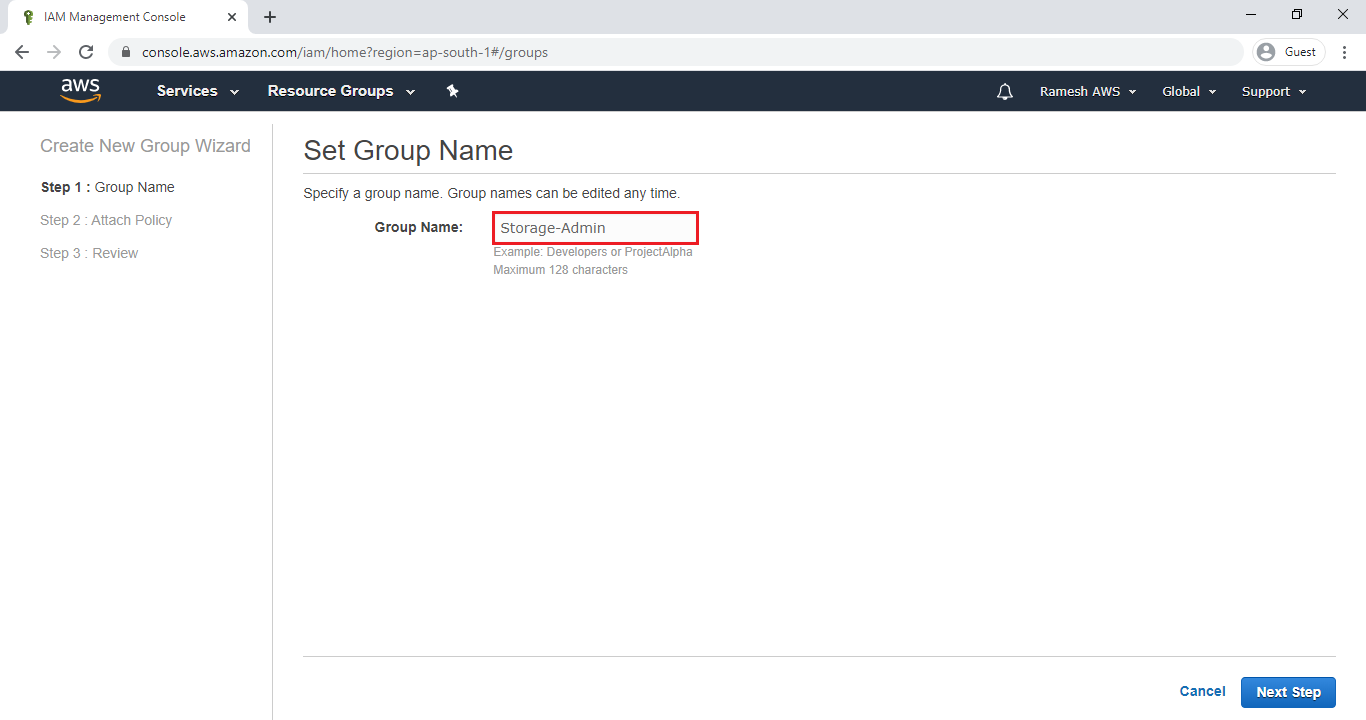
Specify Group Name “Storage-Admin” and click on Next.
Select required policy “AmazonS3FullAccess” to group by searching “s3” in search bar and click on Next.
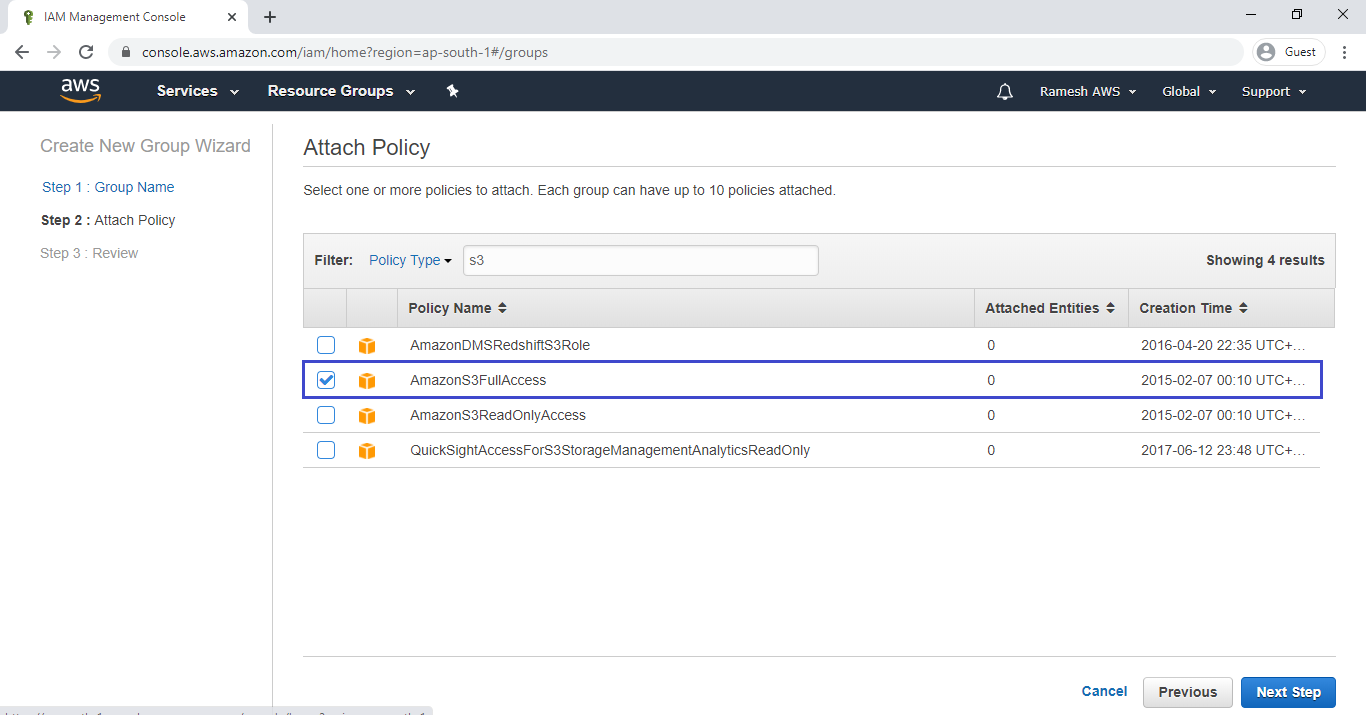
Click on Create Group.
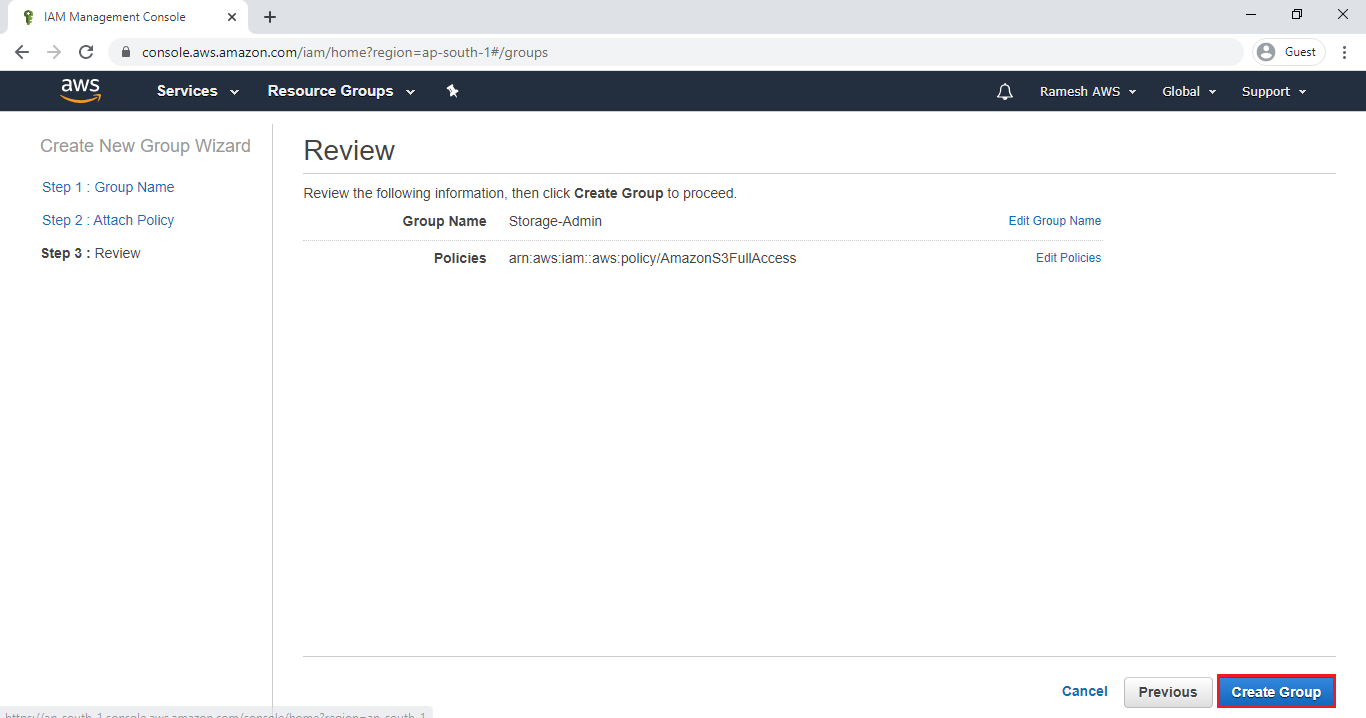
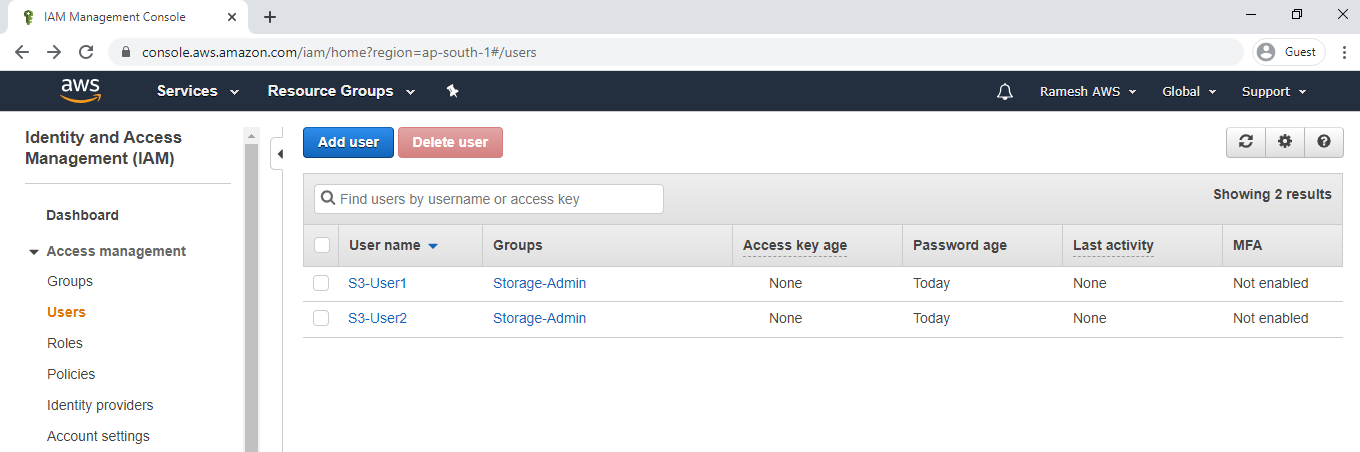
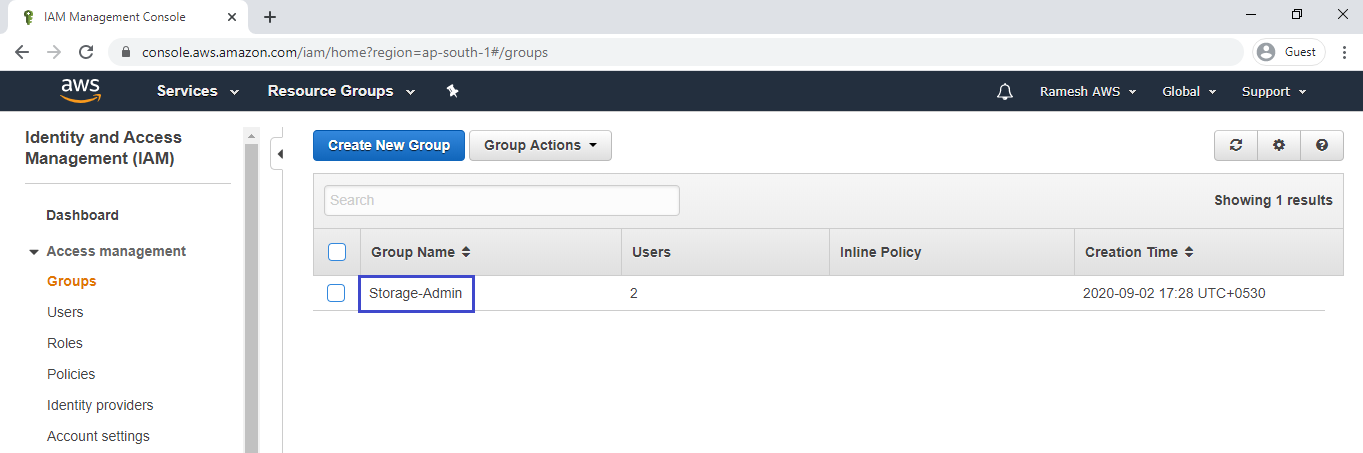
We can the group “Storage-Admin” has been created successfully.
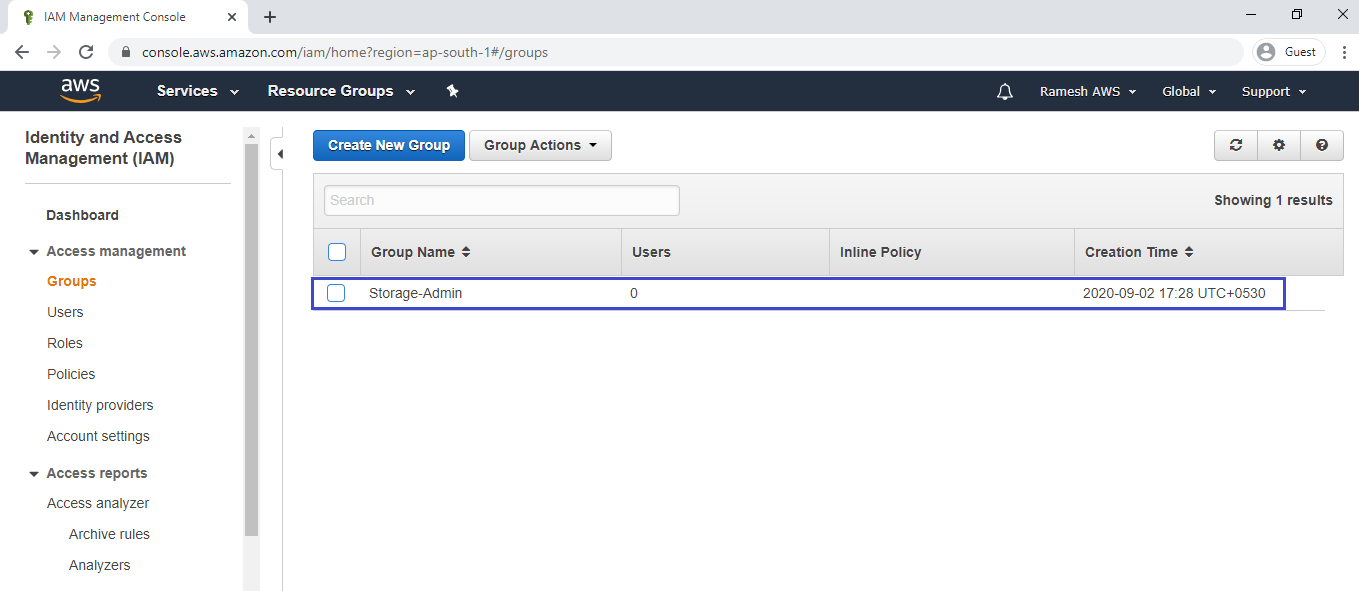
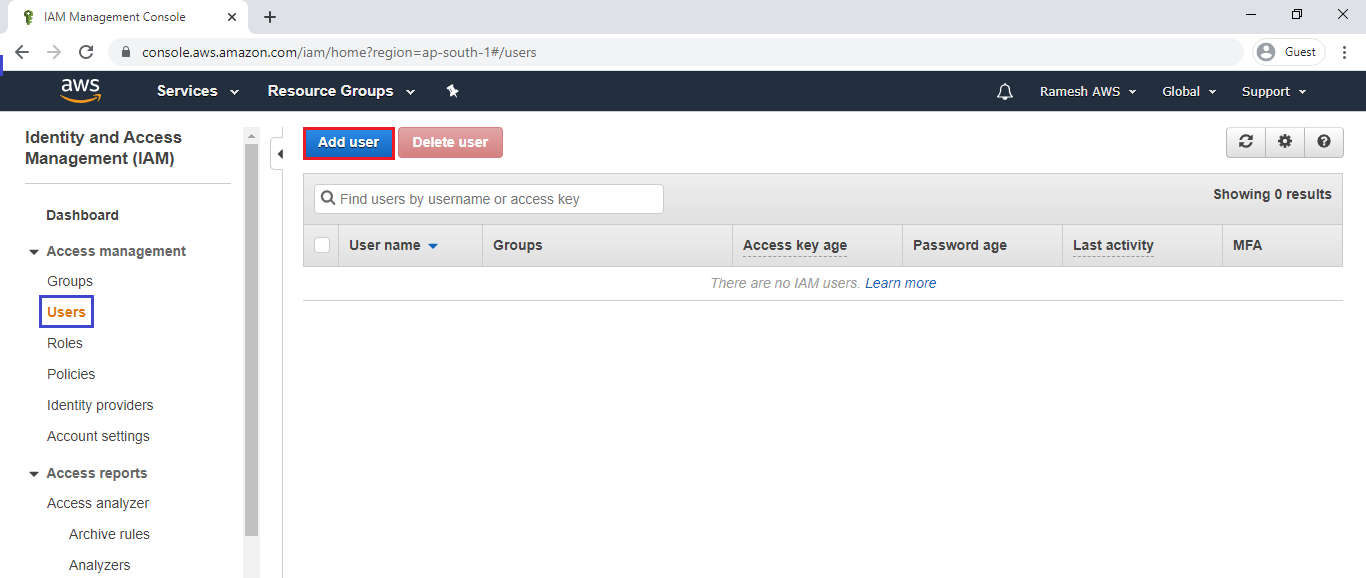
3. Create Users “S3-User1 &S3-User2” and Add to group “Storage-Admin”
Go to Users,click on Add User.
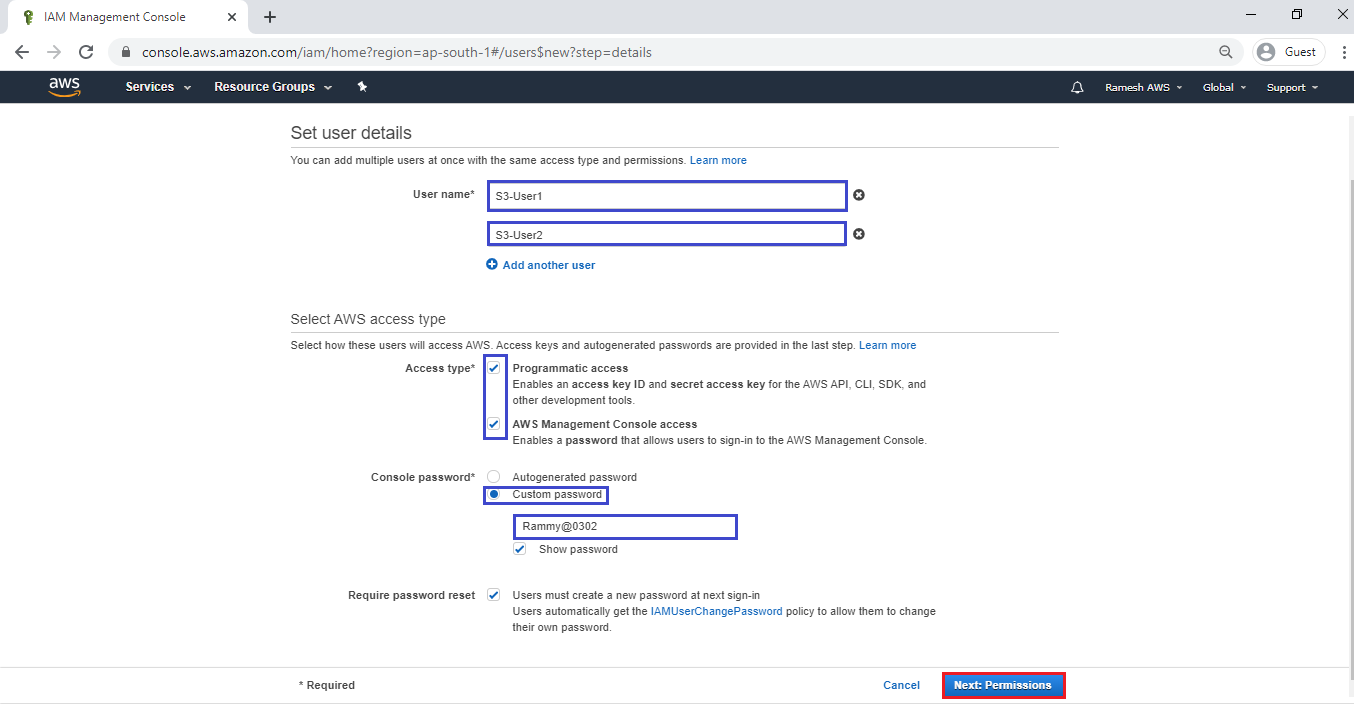
Specify new user names “S3-User1” and “S3-User2”.
Give access type “AWS Management Console Access” and “Programmatic access” to get username and password by clicking on checkbox and click on Next.
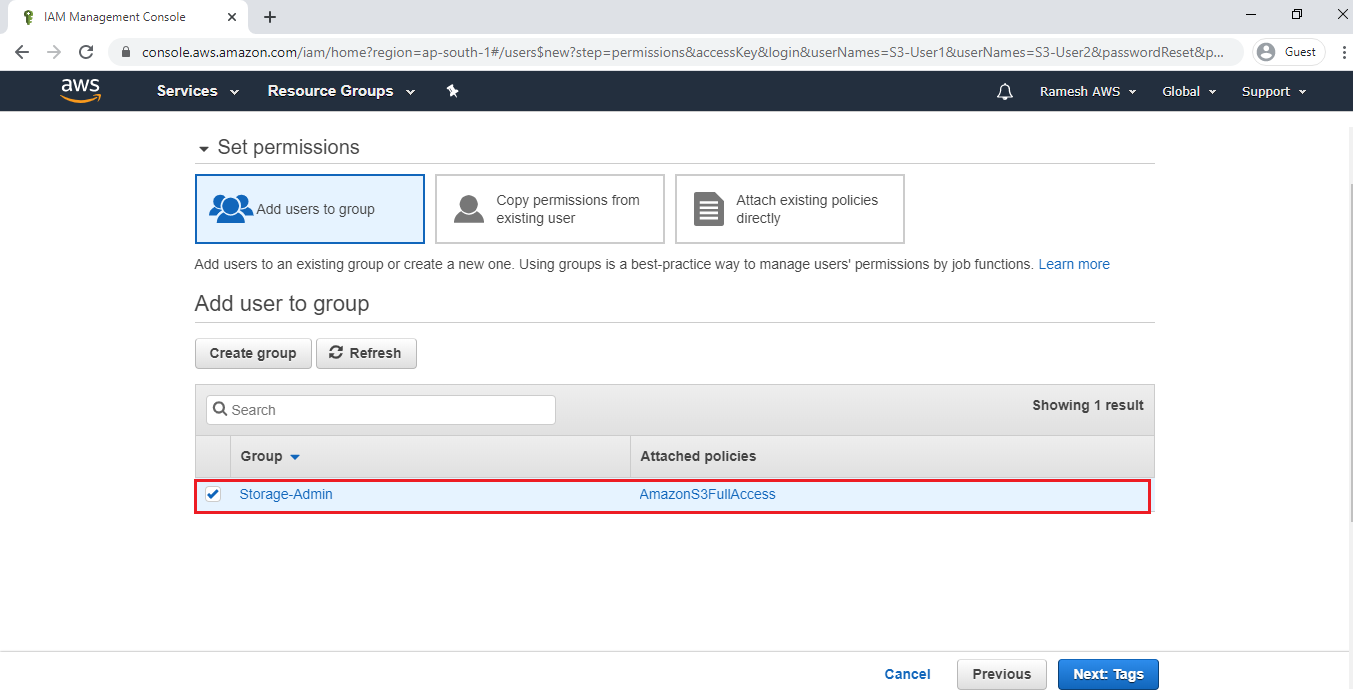
Add users to group “Storage-Admin” and click on Next.
Click on Next.
Click on Create Users.
The users has been created and click on close.
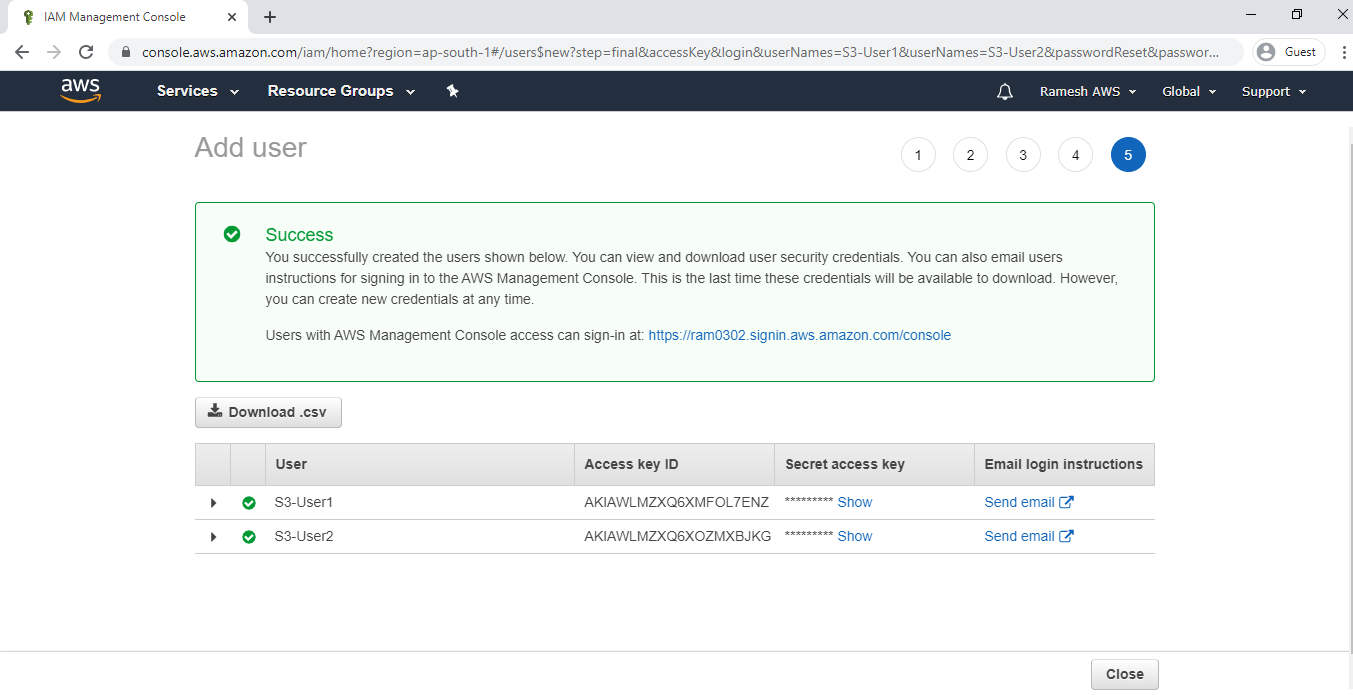
we can see the 2 users added to group.
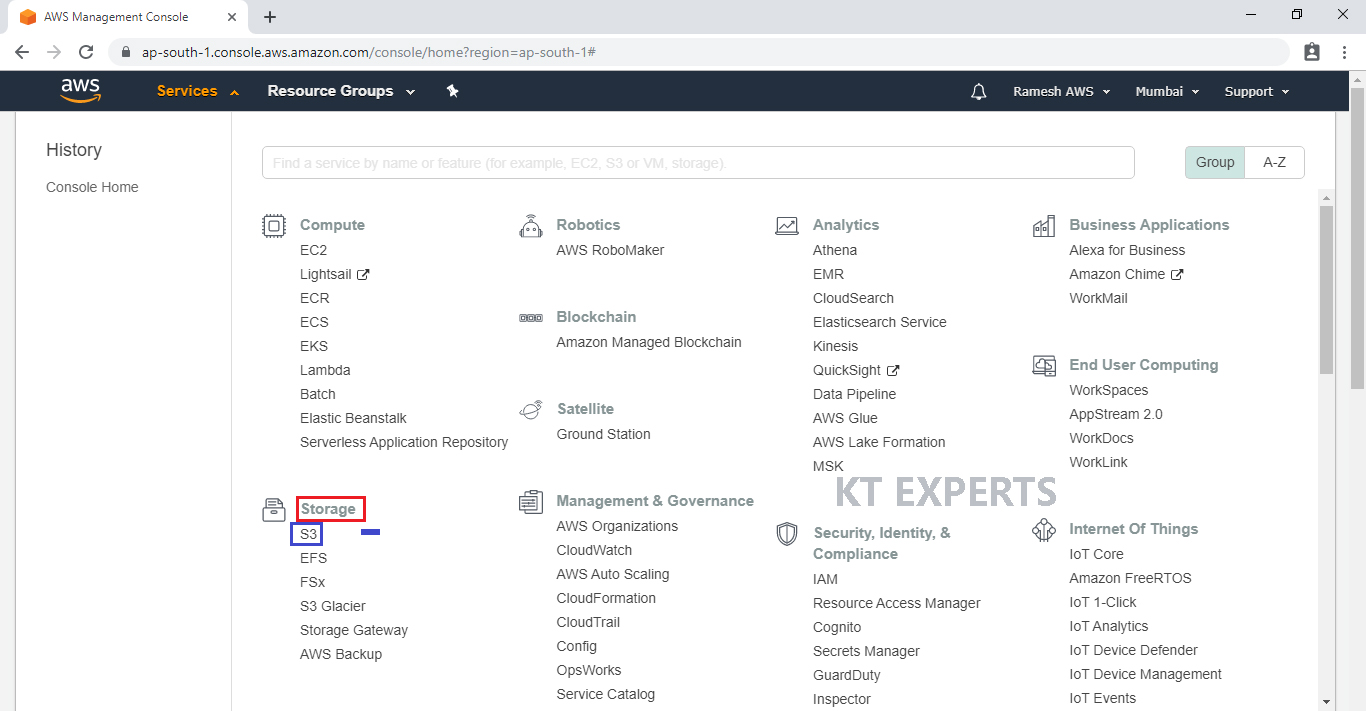
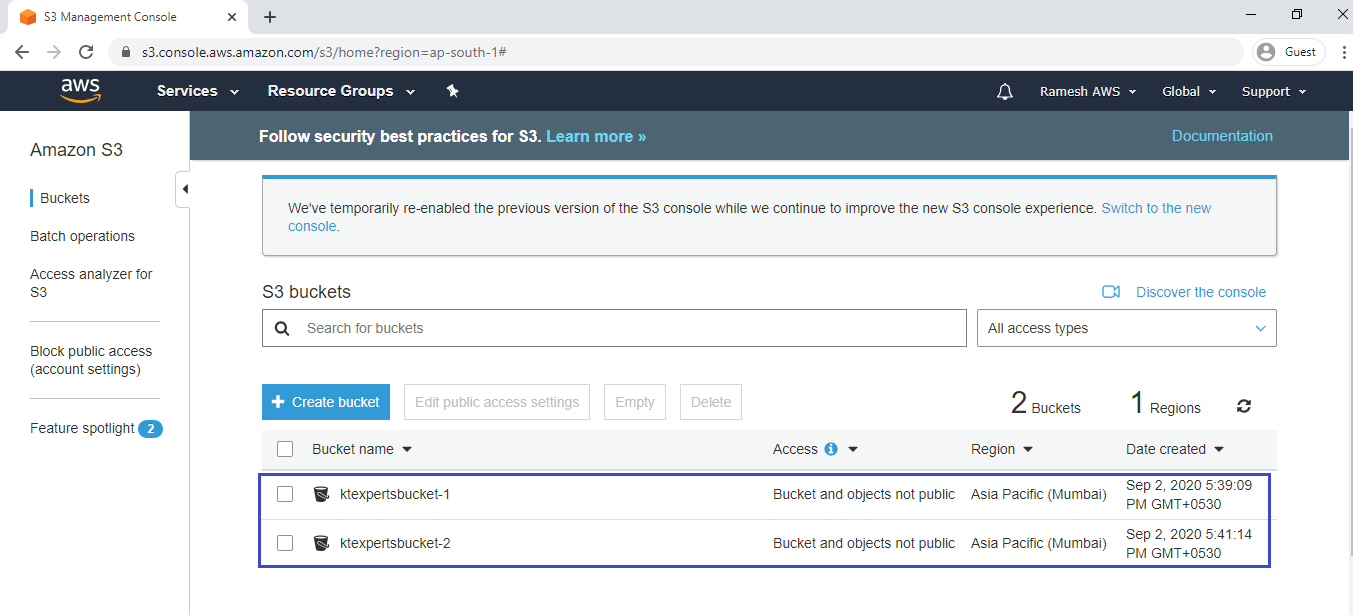
4. Create S3 Buckets “ktexpertsbucket-1 & ktexpertsbucket-2”
Go to Services, under the storage module click on S3 service to open.
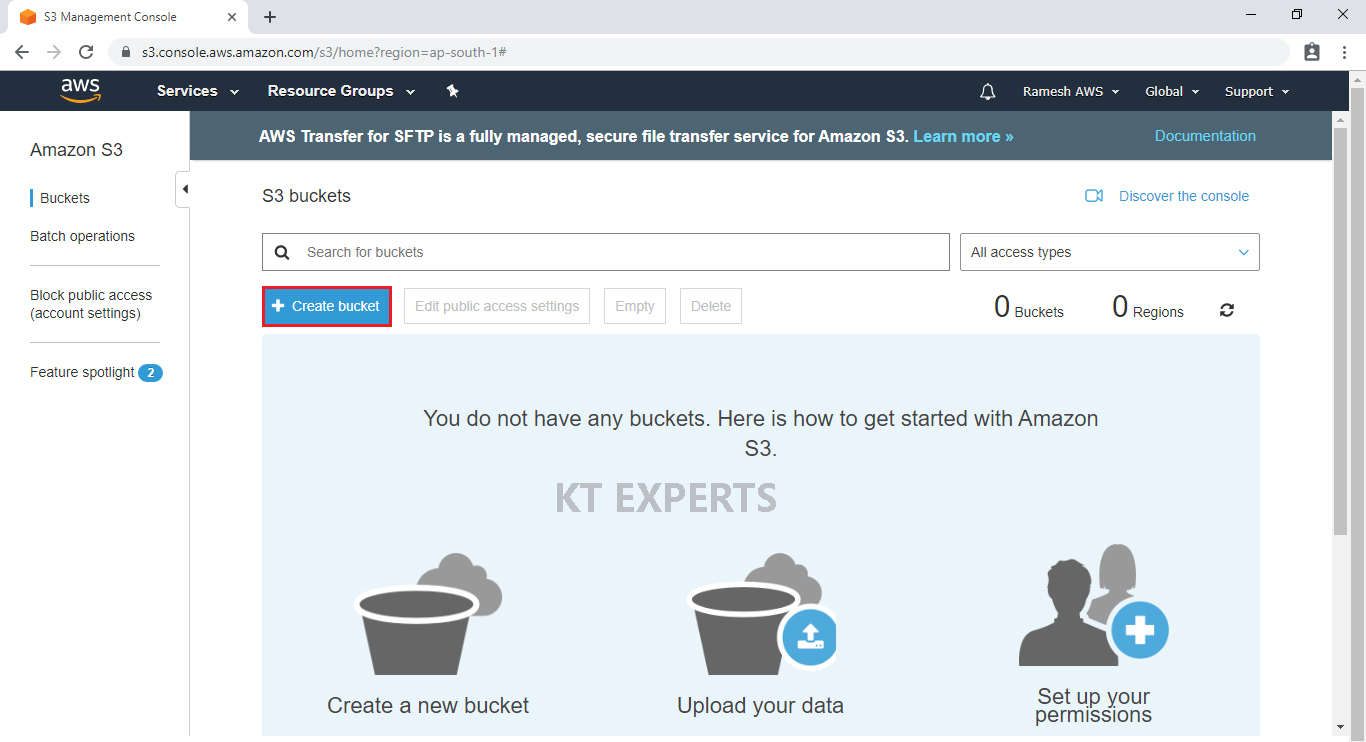
Create First Bucket
Click on create bucket.
Provide the bucket name must be globally unique across all existing bucket name in Amazon S3.
In the Bucket name field we need to follow some guidelines.
- The bucket name can be between 3 and 63 characters long, and can contain only lower-case characters, numbers, periods, and dashes.
- The bucket name must start with a lowercase letter or number.
- The bucket name cannot contain underscores, end with a dash, have consecutive periods, or use dashes adjacent to periods.
- The bucket name cannot be formatted as an IP address (192.81.800.24).
After you have created a bucket, you can’t change its Region.
In Region, Choose required region.
Click on Create.
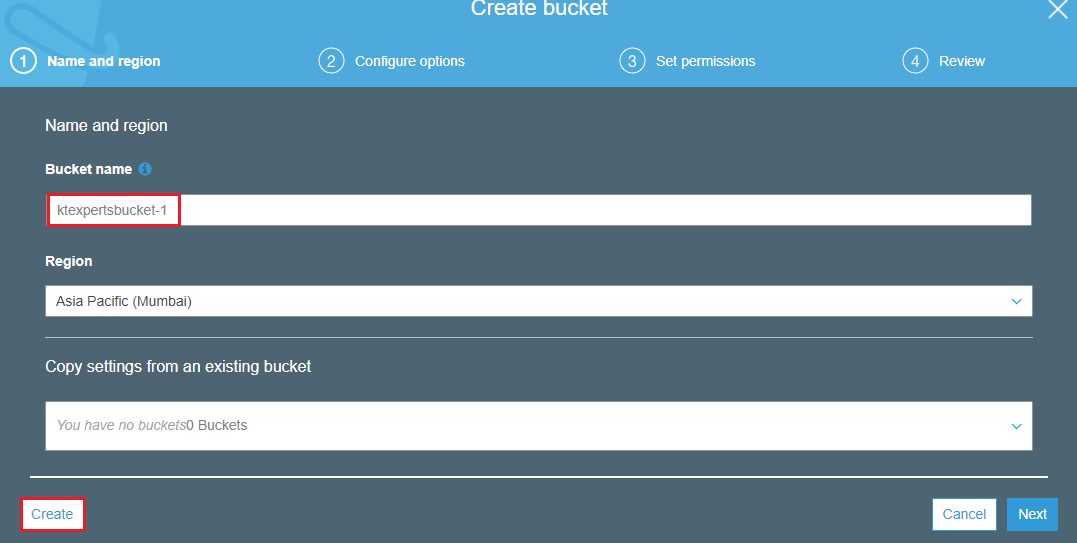
We can see the bucket “ktexpertsbucket-1″ has created successfully.
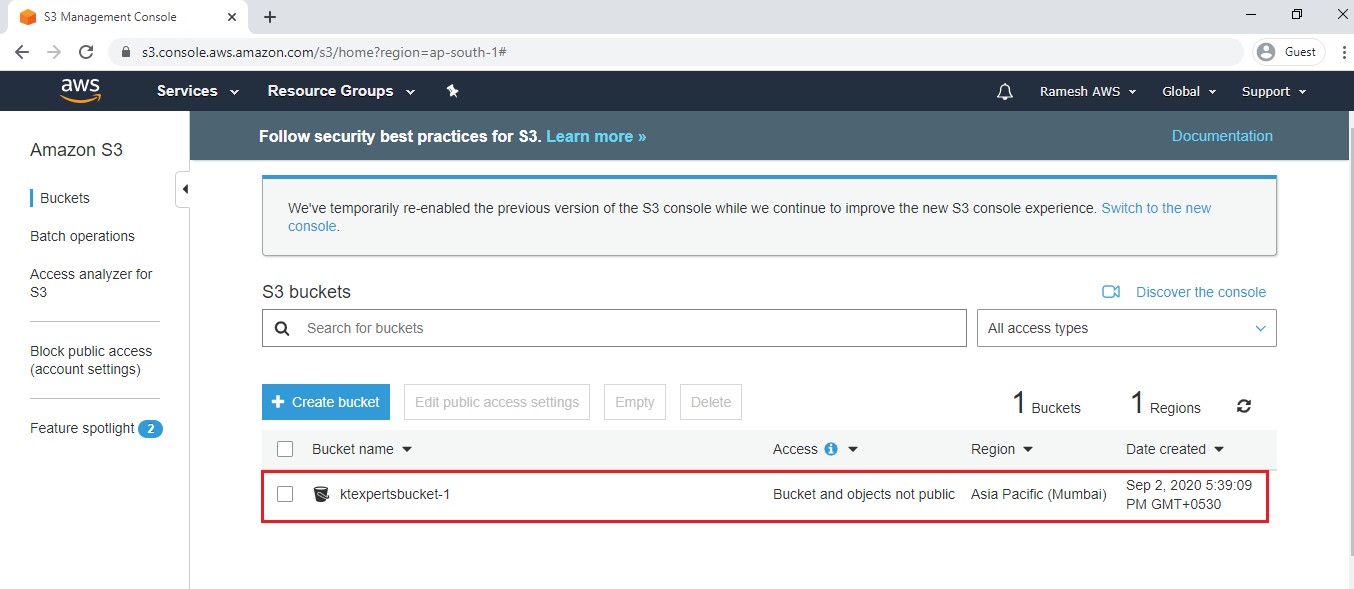
Create Second Bucket
Click on Create bucket.
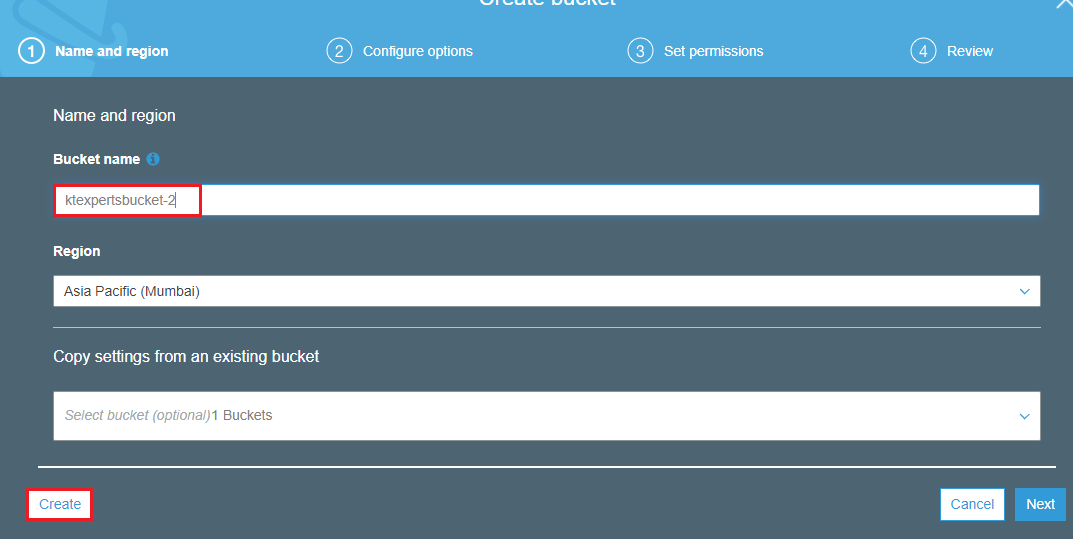
Specify name of the bucket and click on create.
we can see the second bucket “ktexpertsbucket-2” has created successfully.
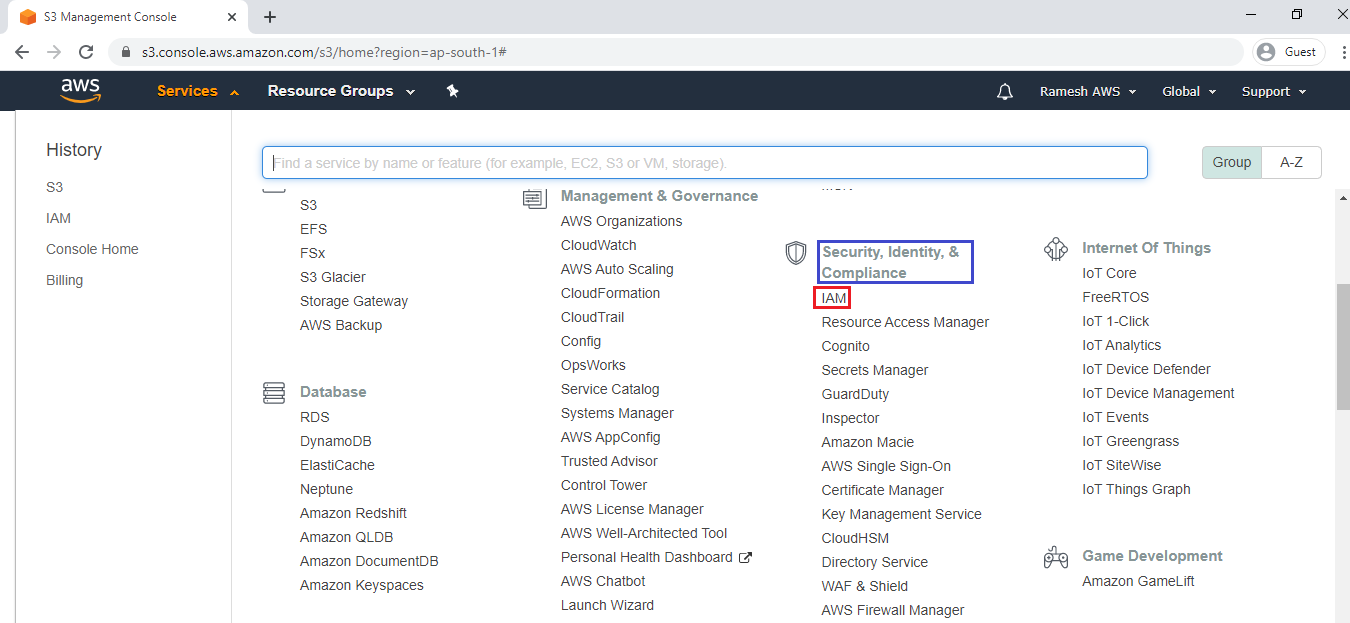
5. Add Inline Policy to Group
Go to Security, Identity & compliance module click on IAM service to open.
Go to group and click on Storage-Admin.
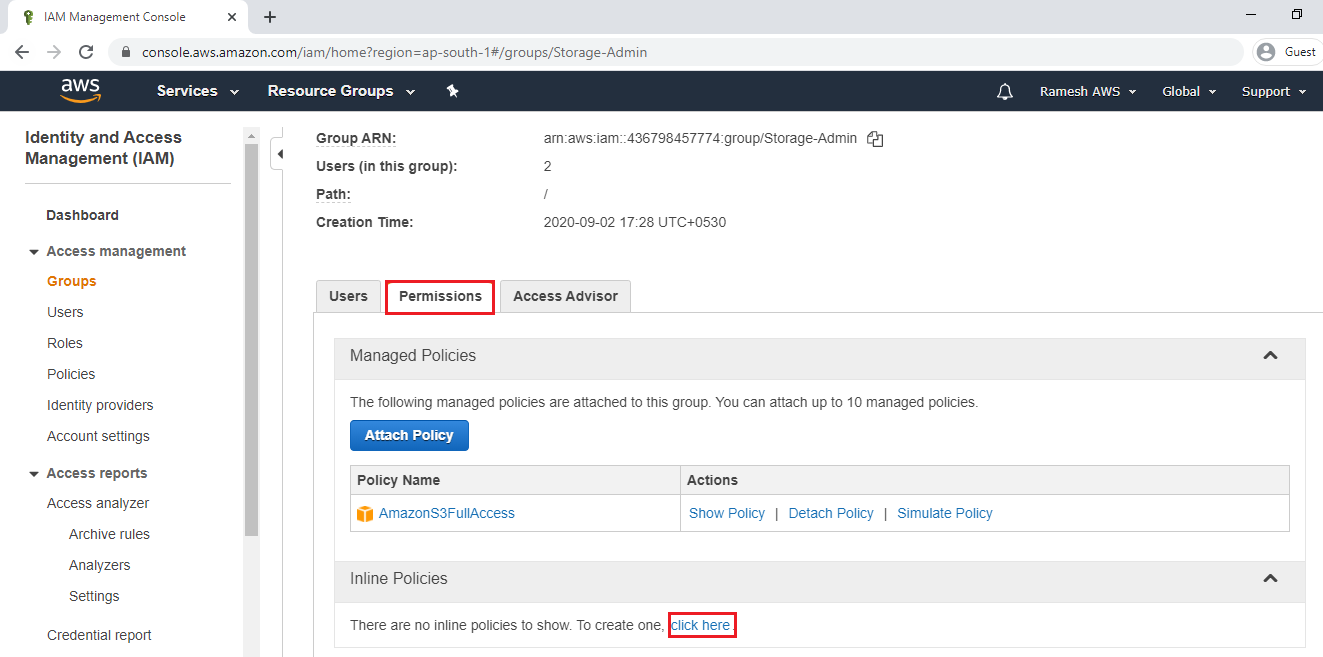
Go to Permission tab and click on inline policy.
Choose Policy Generator and click on select.
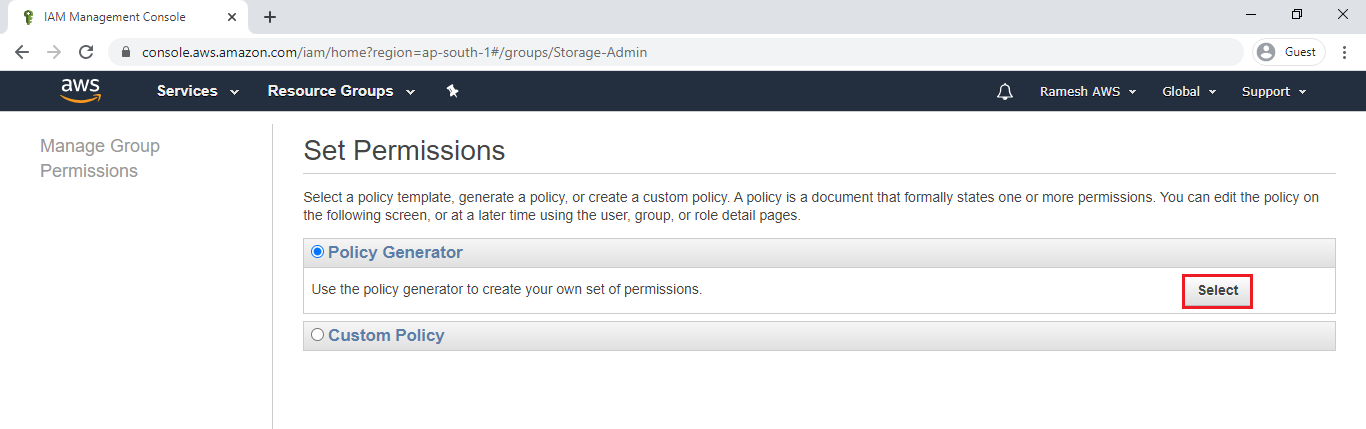
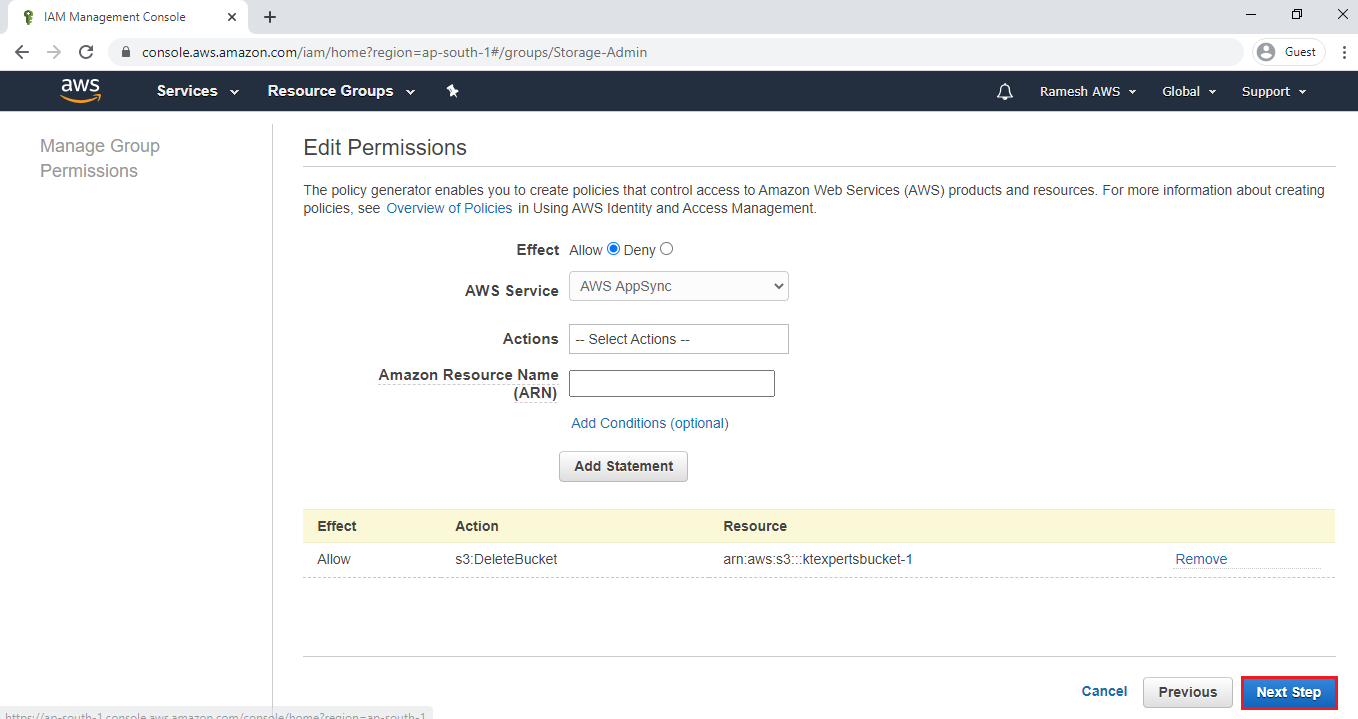
Select Deny of Effect field,Amazon S3 of AWS Service and select Delete Option in the Actions.
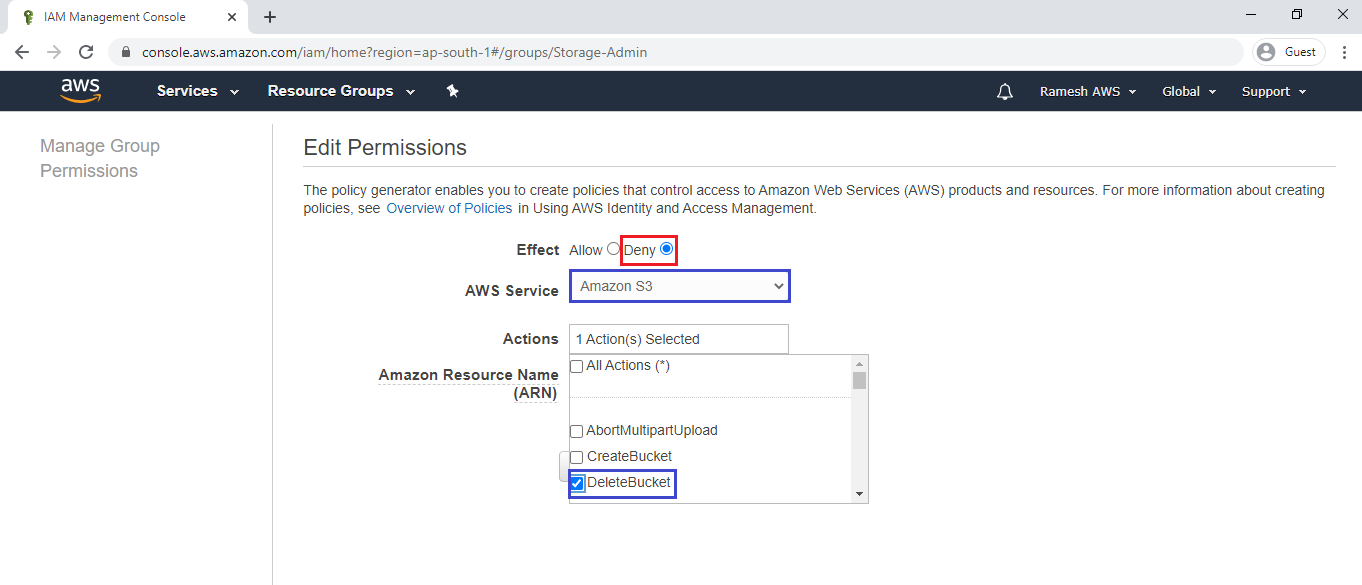
Copy ARN of bucket “ktexpertsbucket-1”
Go inside the S3,select first bucket “ktexpertsbucket-1” and copy Bucket ARN.
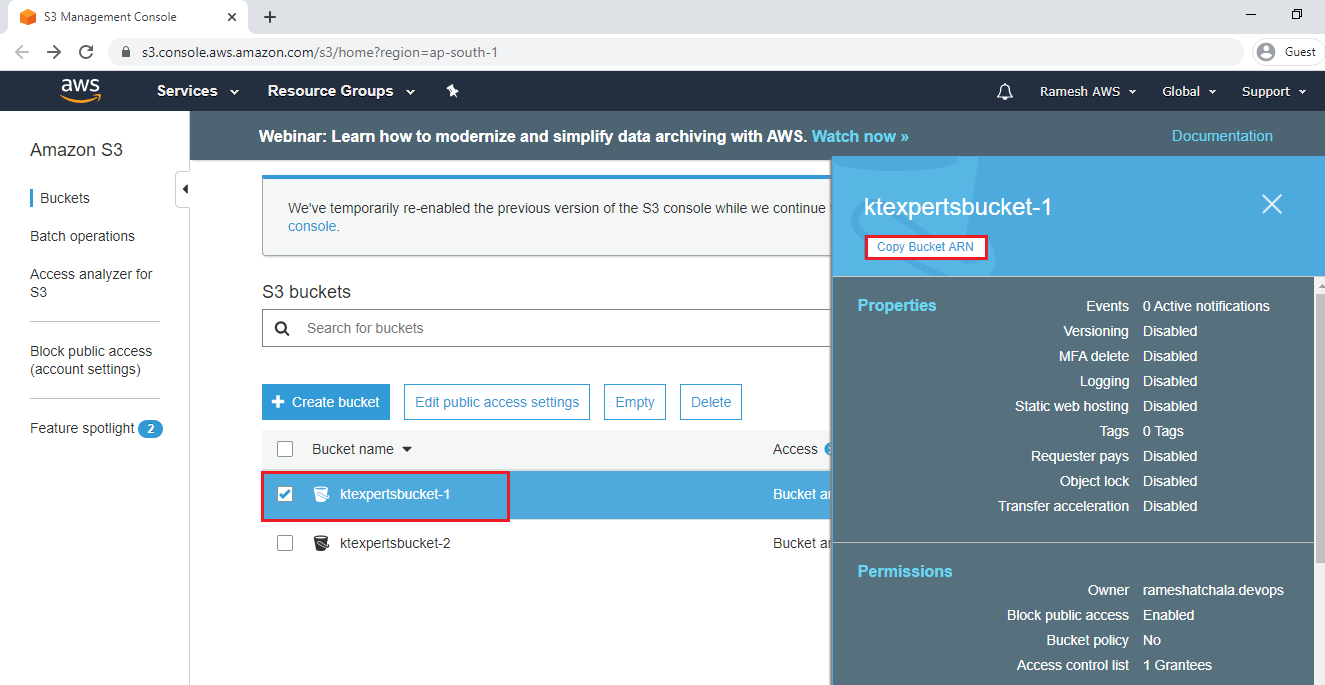
Paste the bucket ARN which was copied and click on Add Statement.
Click on Next Step.
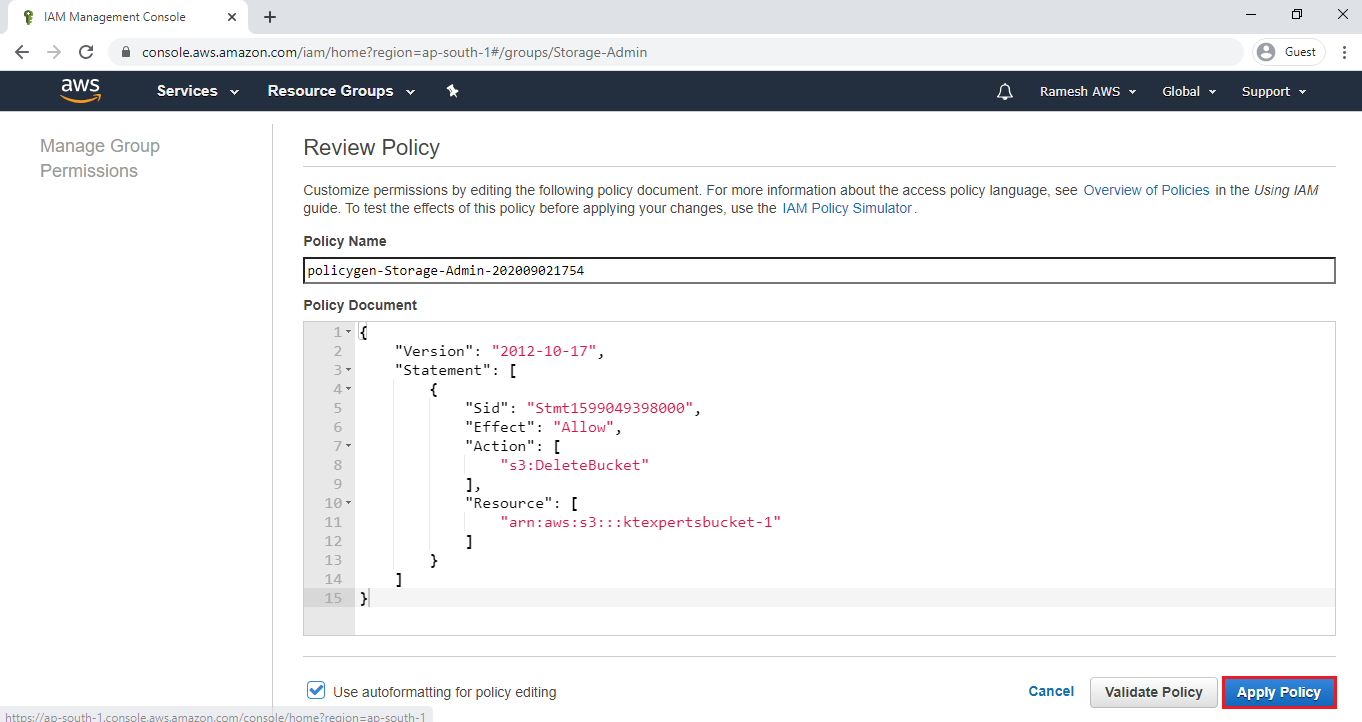
Click on Apply Policy.
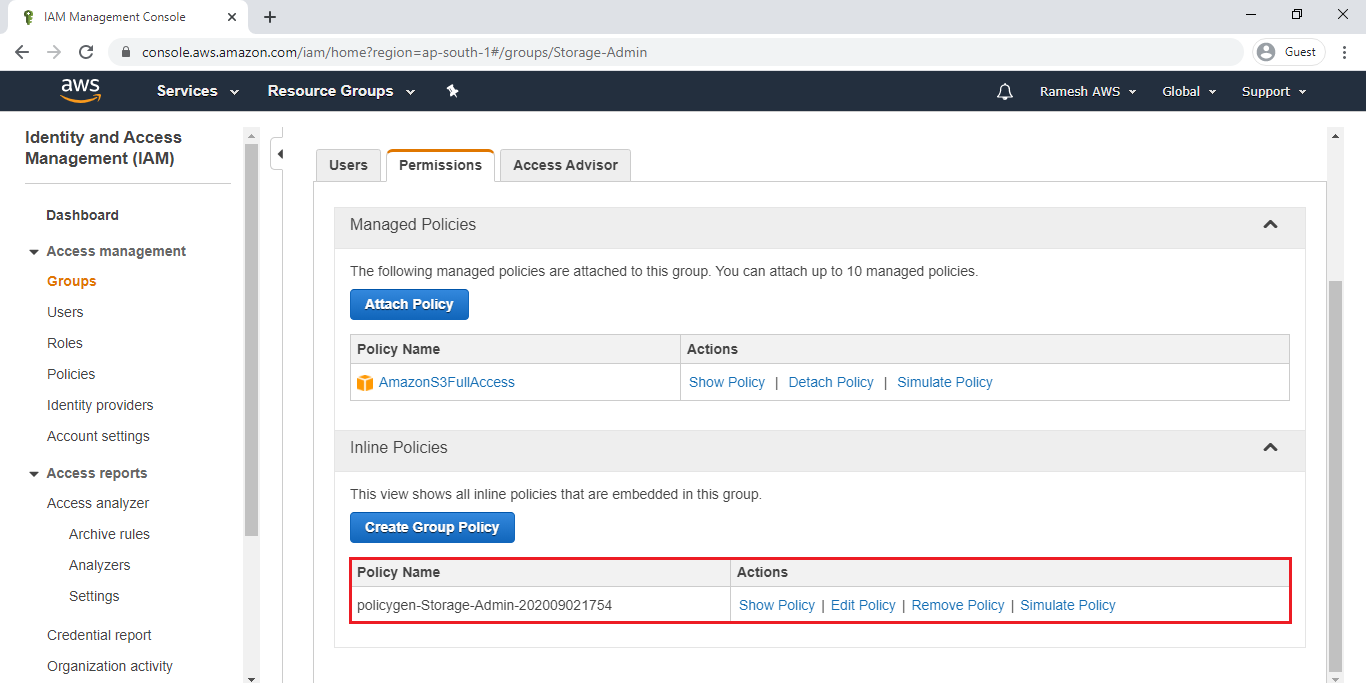
We can see the Inline policy added to the group “Storage-Admin”.
6. Logging to User “S3-User1” and Delete the First Bucket “ktexpertsbucket-1”
Logging to User “S3-User1
Go to IAM,copy IAM users sign-in link.
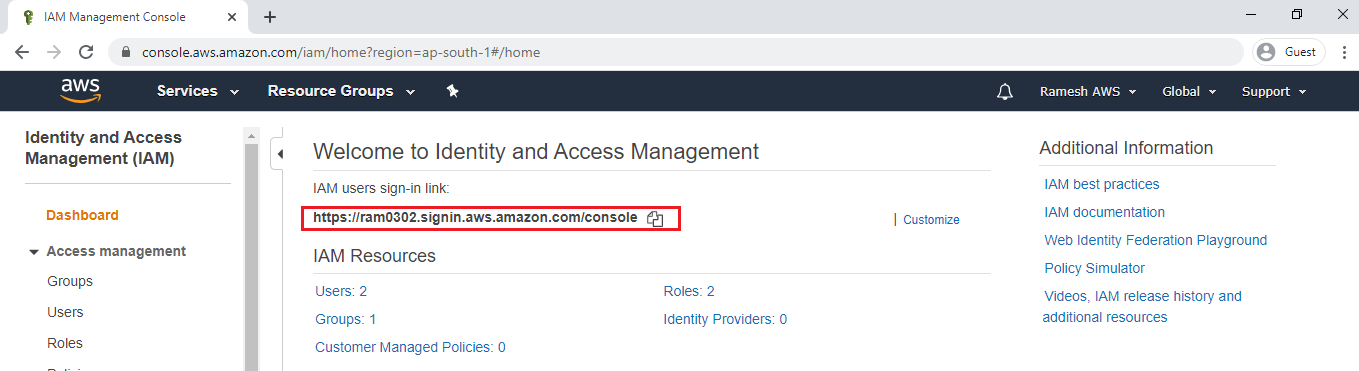
Paste the users sign-in link in another bowser and specify username,password then click on Sign in.
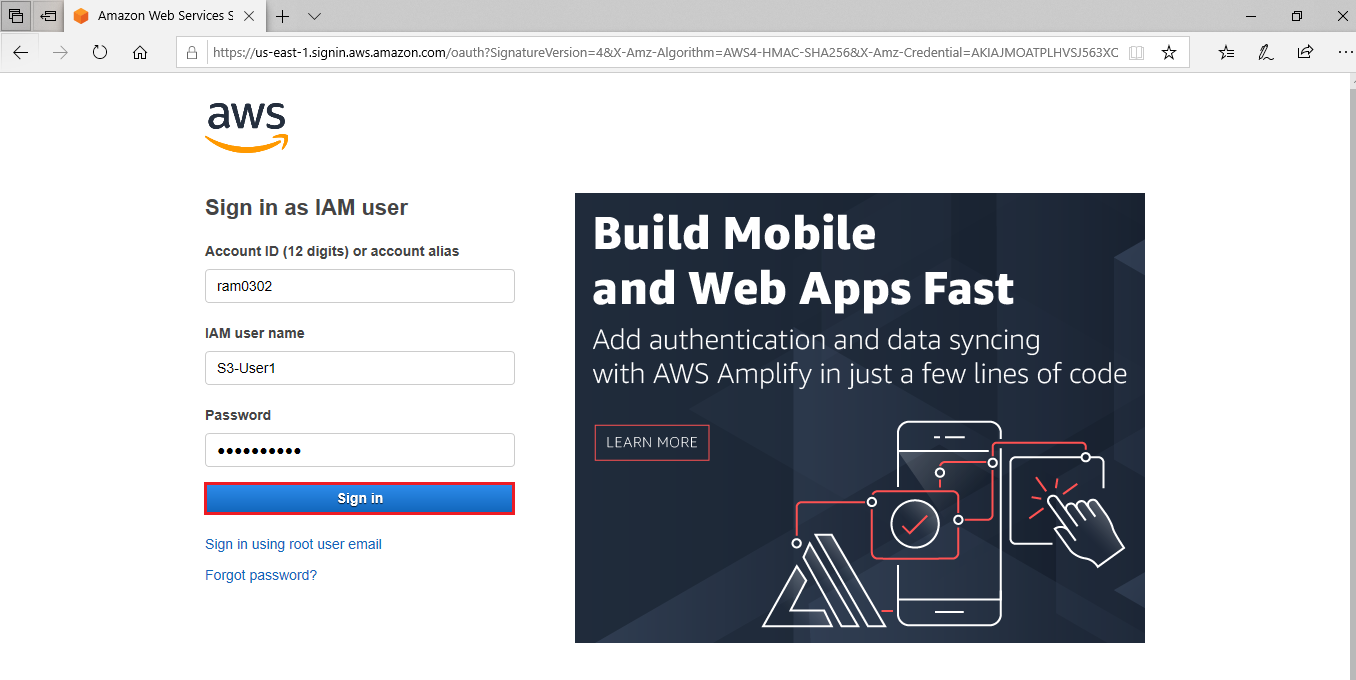
Change the password of user
Specify require password and click on Confirm password change.
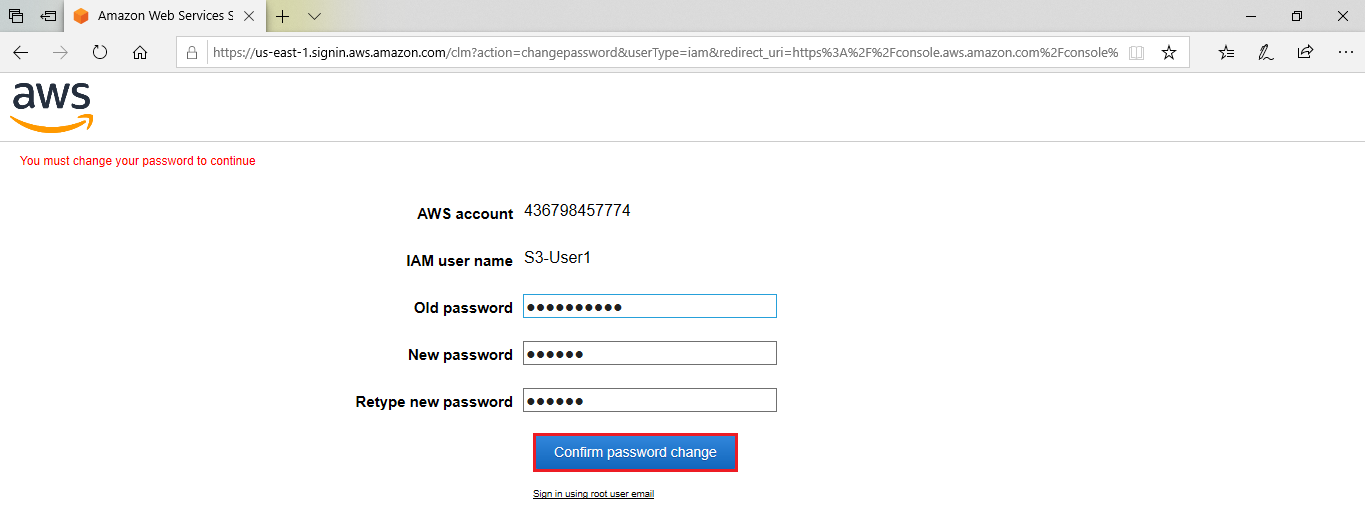
We can see the user “S3-User1@ram0302” and click on S3.
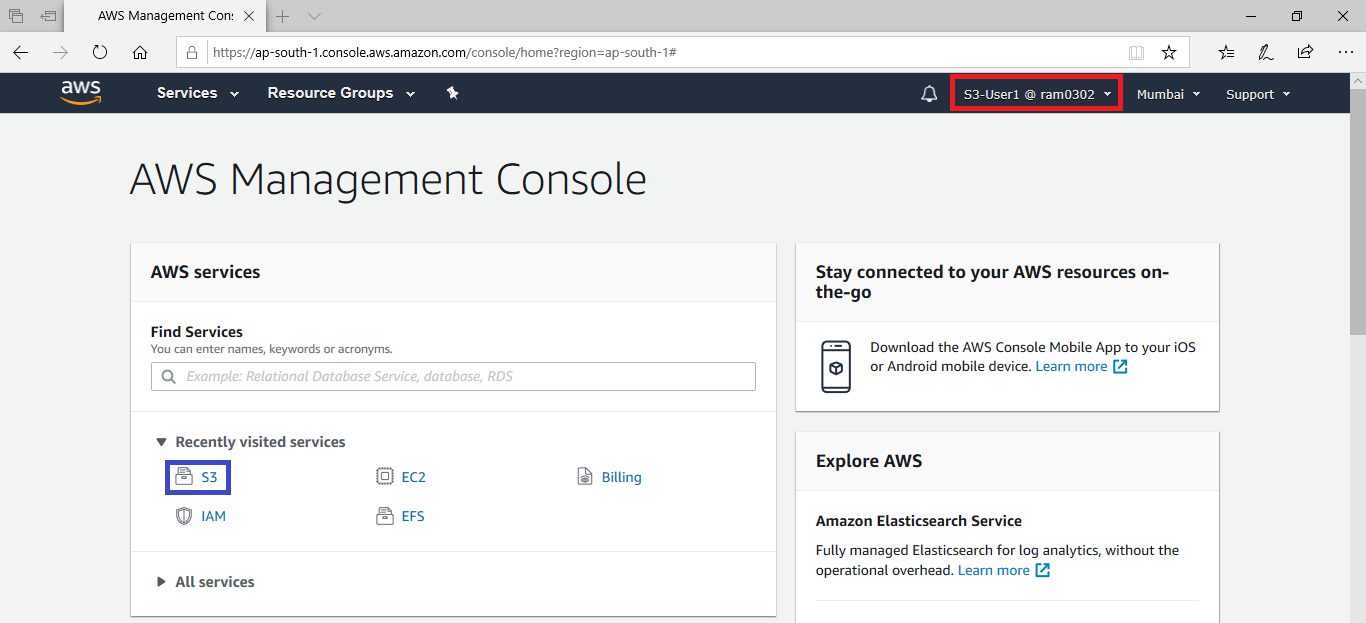
Delete Bucket “ktexpertsbucket-1”
Go inside S3,select first bucket “ktexpertsbucket-1” and click on Delete.
Specify bucketname for deleting and click on Confirm.
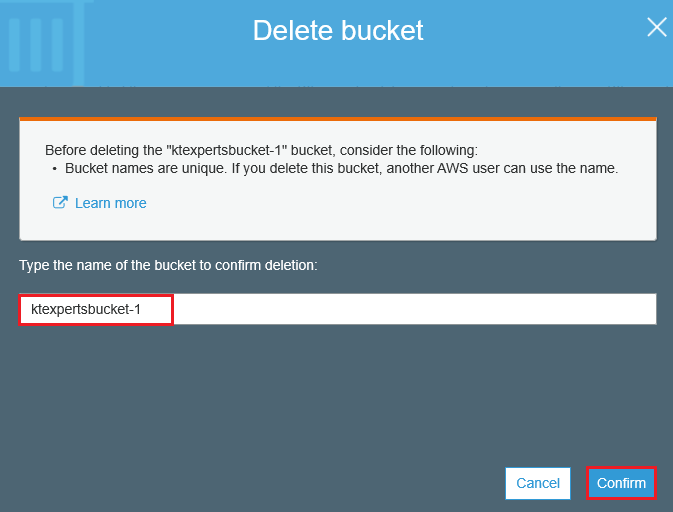
We can see 1Error-Operation failed-Delete bucket Failed.
We can see Access Denied.
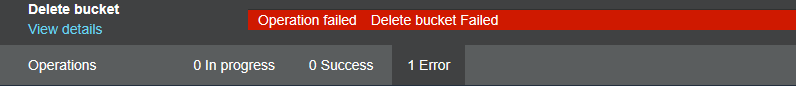
The bucket didn’t delete because we added policy to group “Storage-Admin” so,whoever present in the group those are not able to delete.
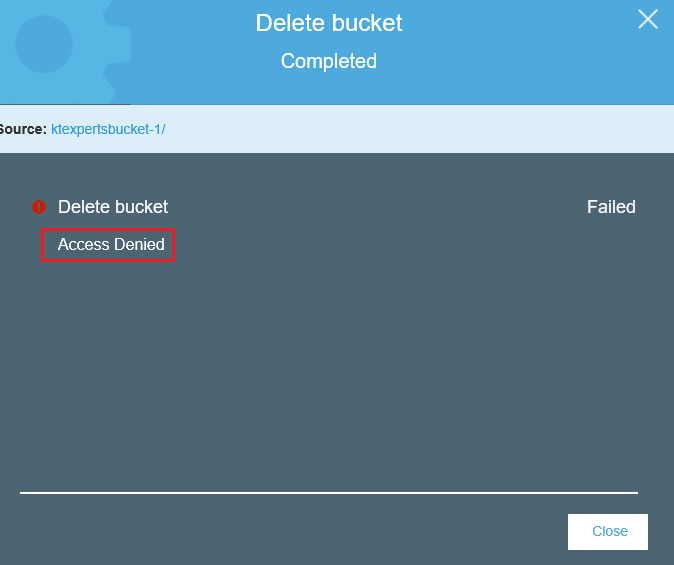
We are unable to delete bucket because we added inline policy to group, so whoever presenting the group they can’t delete the bucket.
Thank you for giving your valuable time to read the above information.
Follow us on
Website : www.ktexperts.com
Facebook Page : KTexperts
Linkedin Page : KT EXPERTS
Follow Me
Ramesh’s Linkedin : Ramesh Atchala