Dear Readers,
In this article,we will see brief explanation regarding to VPC(Virtual Private Cloud).

What is VPC?
- VPC called as Amazon Virtual Private Cloud (VPC).
- It enables you to launch AWS resources into a virtual network that you’ve defined.
- A Virtual Private Cloud is a virtual network dedicated to your AWS account.
- It is logically isolated from other virtual networks in the AWS cloud.
- You can launch your AWS resources, such as Amazon EC2 instances, into your VPC.
- You can configure your VPC.
- You can select its IP address range, create subnets, and configure route tables, network gateways, and security.
- Use a public subnet for resources that must be connected to the Internet.
- Private subnet for resources that won’t be connected to the Internet.
Key Points
- VPC consists of IGWs, Route Tables, NACL, Sub nets and Security Groups.
- 1 Subnet=1AZ.
- Security Groups are Stateful.
- NACLS are Stateless.
- Your VPC automatically comes with a default network ACL and by default it allows all outbound and inbound traffic.
- You can create a custom network ACL by default.
- Each custom network ACL denies all inbound and outbound traffic until you add rules.
VPC Features
- Attach one or more network interfaces to your instances
- Assign multiple IP addresses to your instances
- Assign static private IPv4 addresses to your instances
- Access control lists (ACL)
- Run your instances on single-tenant hardware
- Egress & Ingress filtering
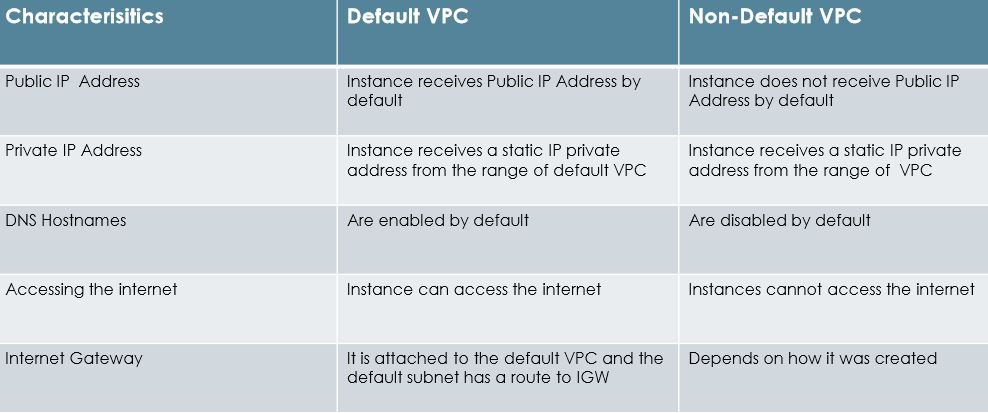
Types of VPC’s
- Default VPC
- Non-Default VPC
VPC Components
- Subnets
- Route Tables
- Internet Gateway
- NAT Gateway
- Security Groups
- Network ACL’s
- VPC Peering
- VPN
Route Tables
- A route table contains a set of rules, called routes, that are used to
- determine where network traffic is directed
- Each subnet in your VPC must be associated with a route table
- The table controls the routing for the subnet.
- A subnet can only be associated with one route table at a time, but
- you can associate multiple subnets with the same route table.
Internet Gateway
An Internet gateway is a horizontally scaled, redundant, and highly
available VPC component that allows communication between instances
in your VPC and the Internet.
Uses:
- Provides a target in your VPC route tables for Internet-routable traffic
- Performs network address translation (NAT) for instances that have been
- assigned public IPv4 addresses.
- An Internet gateway supports IPv4 and IPv6 traffic.
NAT Gateway
- NAT device helps to enable instances in a private subnet to connect to the Internet.
- AWS services, but prevent the Internet from initiating connections with the instances.
- A NAT device forwards traffic from the instances in the private subnet to the Internet
- Other AWS services, and then sends the response back to the instances.
Private, Public and Elastic IP address
- A private IPv4 address is an IP address that’s not reachable over the Internet.
- Private IPv4 addresses are used for communication between instances in the same network.
- A public IP address is an IPv4 address that’s reachable from the Internet.
- You can use public addresses for communication between your instances and the Internet.
- An Elastic IP address is a static public IPv4 address that could be allocate to AWS account.
- KIt could be associated to and from instances as required.
- it’s allocated to the account until you choose to release it.
Subnets
Public Subnet
- A public subnet is a subnet that has access to the Internet through an Internet gateway.
- Each instance has a private address and Public address.
- These instances can communicate with each other, and access the Internet.
Private Subnet
- If a subnet doesn’t have a route to the internet gateway, the subnet is known as a private subnet.
- By default, each instance has a private address, but no public address.
- These instances can communicate with each other, but can’t access the Internet.
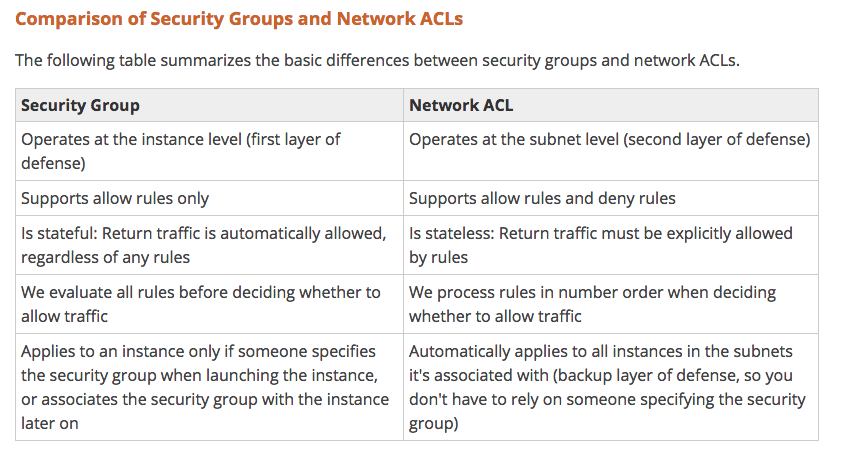
Security
VPC provides features to increase and monitor the
- security for your VPC:
- Security Groups
- Network Access Control Lists (ACLs)
- Flow Logs
Flow Logs
- low Logs enables you to capture information about the IP traffic going to and from network interfaces in your VPC.
- Flow log data is stored using Amazon CloudWatch Logs.
- After you’ve created a flow log, you can view and retrieve its data in Amazon CloudWatch Logs.
You can create a flow log for:
- VPC
- Subnet
- Network Interface
Flow log format:
version account-id interface-id srcaddr dstaddr srcport dstport protocol packets bytes start end
action log- status.
VPC Peering
- VPC peering is a networking connection between two VPCs that enables you to route traffic between them.
- Instances in either VPC can communicate with each other as if they are within the same network.
- Create a VPC peering connection between own VPCs, or with a VPC in another AWS account.
- In both cases, the VPCs must be in the same region.
Network ACL
- Each subnet in your VPC must be associated with a network ACL.
- If you don’t explicitly associated a subnet with a network ACL,the subnet is automatically associated with the default network ACL.
- You can associate a network ACL with multiple subnets; however, a subnet can be associated with only one network ACL at a time.
- When you associate a network ACL with a subnet, the previous association is removed.
- A network ACL contains a numbered list of rules that is evaluated in order, starting with the lowest numbers rule.
- A network ACL has separate inbound and outbound rules, each rule can be either allow or deny traffic.
VPN
- Connect VPC to corporate data center using VPN connection.
- This makes the AWS cloud an extension of your data center.
- VPN connection consists of a virtual private gateway and a customer gateway.
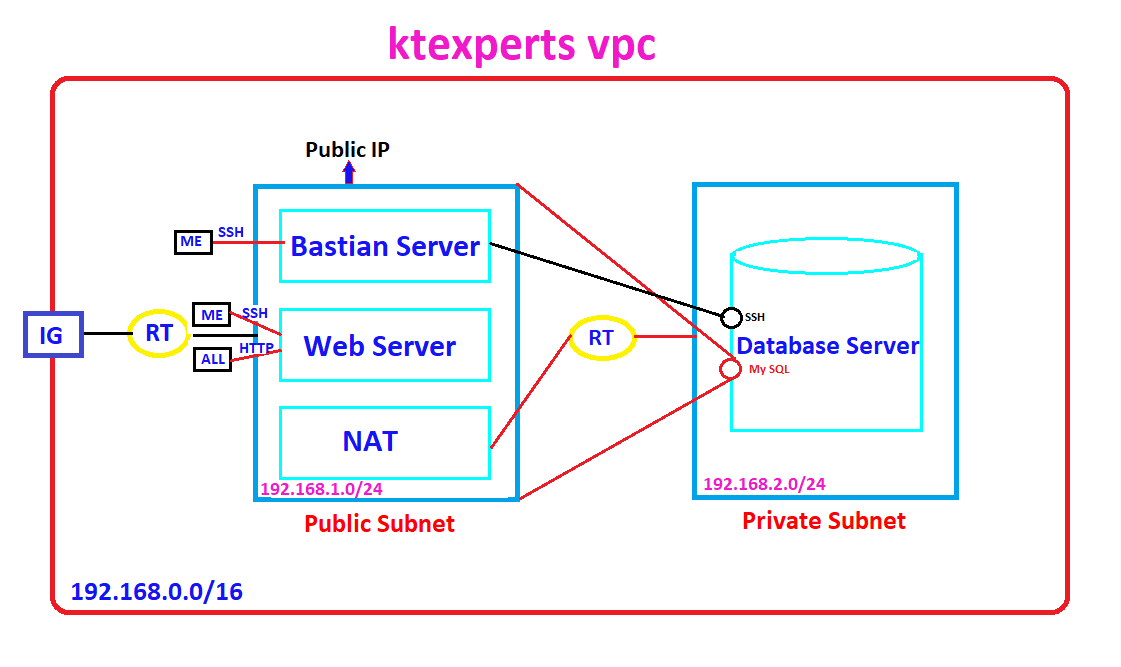
I have divided Creating VPC into multiple articles,please check below steps along with article links.
STEP 1
Create VPC and assign IP range.
Create two subnets inside the VPC and assign IP range for both subnets.(By default two subnets are private).
Create Internet Gateway for providing internet to the subnet -1.
Create Route Table.
One end of the Route Table has connect to the Internet Gateway and another end of Route Table connect to public subnet.
Amazon Virtual Private Cloud in AWS (Amazon Web Services) (PART – 1)
STEP 2
Create Web Server inside public subnet.
Amazon Virtual Private Cloud in AWS (Amazon Web Services) (PART – 2)
STEP 3
Create Database Server inside private subnet for keeping sensitive information inside the database.
Amazon Virtual Private Cloud in AWS (Amazon Web Services) (PART – 3)
STEP 4
Create Bastian Server inside public subnet for connecting to database server.
Amazon Virtual Private Cloud in AWS (Amazon Web Services) (PART – 4)
STEP 5
Copy database server pem file to bastian server through WinSCP tool.
Create NAT Gateway for providing internet to database server(To install updates and required packages).
Create Route Table.
Attach both side of the Route Table connect to NAT Gateway and Private Subnet.
Connect to database Server through Bastion Server then install packages.
Amazon Virtual Private Cloud in AWS (Amazon Web Services) (PART – 5)
Thank you for giving your valuable time to read the above information. Please click here to subscribe for further updates
KTEXPERTS is always active on below social media platforms.
Facebook : https://www.facebook.com/ktexperts/
LinkedIn : https://www.linkedin.com/company/ktexperts/
Twitter : https://twitter.com/ktexpertsadmin
YouTube : https://www.youtube.com/c/ktexperts
Instagram : https://www.instagram.com/knowledgesharingplatform


 (1 votes, average: 4.00 out of 5)
(1 votes, average: 4.00 out of 5)

